
Cyber attackers have compromised hundreds of CMS sites running WordPress or Joomla and “well-known” hidden directories to serve up Shade ransomware and phishing pages in the wild.
The Shade/Troldesh ransomware has been spotted by Zscaler as “quite active” in the wild over the past month and has been spreading via compromised WordPress and Joomla sites. The impacted WordPress sites were running versions 4.8.9 to 5.1.1.
According to Zscaler security researchers, the bad actors are potentially exploiting older plugins, themes or server-side software and taking advantage of a “well-known” hidden directory on the HTTPS website. The actors use the hidden directory to host and distribute the Shade ransomware and phishing pages.
Zscaler further described how the attackers use the hidden directory “well-known” (/.well-known/) commonly used by website owners to demonstrate ownership of a domain to Certificate Authorities (CAs). CAs will scan this “well-known” directory for a placed token and code on the system to validate the domain.
Zscaler said their cloud service blocked web transactions for compromised WordPress or Joomla sites impacted by Shade payloads and phishing pages at 13.6% and 27.6% respectively.
Zscaler also provided a breakdown of the types of malware detected in the hidden directory over the past month:
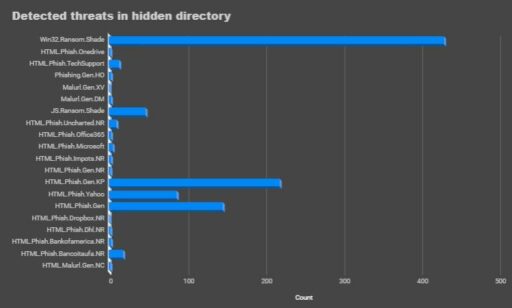
Two specific use cases were also described in the blog, to include how attackers are using the hidden directory and three types of files (ZIP, HTML and EXE disguised as jpeg file) to distribute malware and phishing pages.
The first use case describes how the actors use the /.well-known/pki-validation directory to host several malicious ZIP files. Two HTML files inst.htm and thn.htm redirect to download the ZIP files that contain javascript file used to execute and download the malicious payload.
The other use case involves how phishing pages were hosted on the compromised sites, using well-known brands to include Office 365, Microsoft, DHL, Dropbox, Bank of America, Yahoo, Gmail, among others.
