A new botnet dubbed “GoldBrute” targets 1.5 million publicly exposed RDP servers on the internet via brute force attack.
Security researchers from Morphus Labs spotted the malicious botnet targeting internet-exposed RDP servers via a seven-stage brute force attack. Consequently, the bad actors are likely looking for weak passwords used to compromise RDP servers on the internet.
Also, Shodan lists nearly 2.4 million exposed RDP servers. So, this is a large number of RDP servers that could be at high risk of compromise or exposure to similar attacks.
Most noteworthy, just a single command and control server controls the GoldBrute botnet. In addition, the botnets transfer data via AES encrypted WebSocket connections over port 8333.
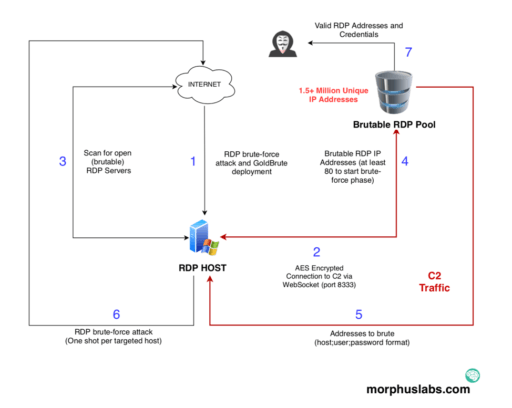
Renato Marinho of Morphus Labs describes how the GoldBrute attack takes place in seven steps as outlined below (see Figure A):
- RDP brute-force attack and compromise of exposed RDP server. Attacker installs java-based GoldBrute botnet malware.
- An AES encrypted connection established to command and control (C2) server via WebSocket (port 8333).
- Next, the bot will scan internet for additional “brutable” exposed RDP server targets.
- After bot reaches 80 brutable RDP servers, it then starts the brute-force phase.
- Receive “host + username + password” combinations
- Brute force hosts with the same combinations identified in previous step
- Finally, attackers will gain access to final valid RDP addresses and combinations.
At the time of the report, it is unknown how many of the 1.5 million servers could have been compromised.
This is the latest threat that highlights the importance of not exposing RDP servers to the internet. This also comes in the wake of “BlueKeep” vulnerability CVE-2019-0708 patched by Microsoft last month.
Security experts have been warning of scanning activity picking up and automated exploits are right around the corner.
