Attackers are targeting open Android Debug Bridge (ADB) ports running on Android devices to install cryptocurrency-mining botnet malware.
In a report last week, Trend Micro spotted the malicious activity in 21 different countries. The company said attackers take full advantage of open ADB ports to deliver the mining botnet and also spread via SSH.
“This attack takes advantage of the way open ADB ports don’t have authentication by default, similar to the Satori botnet variant we previously reported. This bot’s design allows it to spread from the infected host to any system that has had a previous SSH connection with the host,” Trend Micro said.
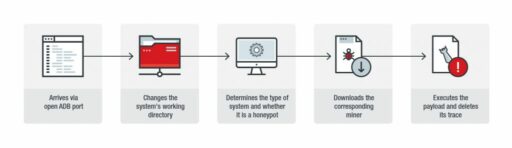
According to Trend Micro, the ADB attacks works in five steps (also see Figure A):
- Malicious IP targets devices with open ADP port
- Attack uses the ADB command shell to change the victim system’s working directory to “/data/local/tmp”.
- Attacker determines what type of system it is.
- Downloads the corresponding miner (note: three were listed in this attack).
- Finally, attack executes the payload and deletes any trace of the malware.
Of course, ADB is a useful Android device feature administrators and developers. However, the attacks serve as reminder not to leave open or unnecessary ports open on your device unless absolutely necessary.
