
Researchers at Microsoft have revealed details on a new fileless info-stealing campaign that uses Astaroth malware.
Microsoft spotted a sharp increase in the malicious use of WMIC utility used to run malicious scripts and evade detection. Windows Management Instrumentation Command-line (WMIC) is a command-line interface for WMI. The built-in utility is also compatible with existing shells and utility commands.
The campaign activity spiked between May and June of this year (see figure 1) and used Astaroth, a backdoor malware that runs directly in memory. To add, Astaroth is notorious for “living off the land.” In other words, the malware uses built-in system tools to run malicious code and without having to drop executable files on disk.
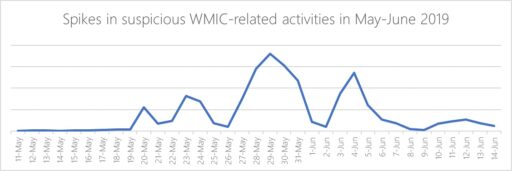
Security firm Cybereason initially discovered Astaroth in February this year. In those attacks, the company noticed Astaroth abused native OS processes and exploited security-related products (such as anti-virus). In addition, the malware is notorious for stealing sensitive information such as credentials and exfiltrates data to the remote attacker.
Living off the Land
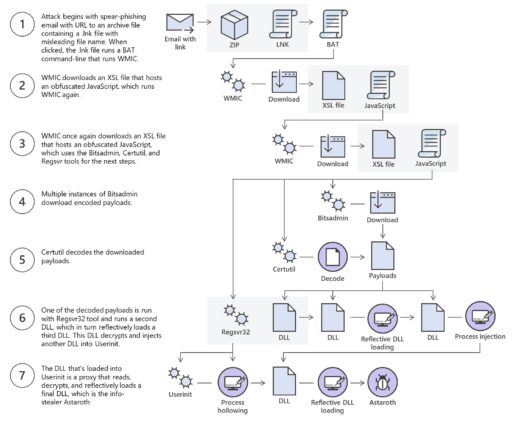
Andrea Lelli of Microsoft’s Defender ATP Research team described “living off the land” attack chain in seven steps (see Figure 2):
- Spear phishing email with malicious URL to an archive file containing a .lnk file. Once clicked by user, the .lnk file runs a BAT command line that runs WMIC.
- WMIC downloads an XSL file that hosts an obfuscated JavaScript to run WMIC again.
- WMIC again downloads an XSL file that hosts an obfuscated JavaScript (used for running tools in next steps).
- Multiple instances of Bitsadmin utility download malicious payloads.
- Certutil (built in utility) decodes the downloaded payloads.
- One of the payloads is run with Windows Regsvr32 tool and runs a second DLL (which then runs a third DLL file). The latter DLL then decrypts and injects another DLL into Userint.
- This last DLL is also used as a proxy to read, decrypt and load Astaroth trojan.
Lelli also made a good comparison of the fileless attacks to the H.G. Wells’ popular novel The Invisible Man. In the analogy, Lelli references just because you’re invisible, doesn’t mean you’re undetectable.
“Abusing fileless techniques does not put malware beyond the reach or visibility of security software,” Lelli added.
“On the contrary, some of the fileless techniques may be so unusual and anomalous that they draw immediate attention to the malware, in the same way that a bag of money moving by itself would.”
Microsoft concluded that advanced anti-malware solutions, like Microsoft Defender ATP, can expose fileless threats like Astaroth.
