
The National Institute of Standards and Technology (NIST) has issued new Security-Focused Configuration Management of Information Systems guidelines (SP 800-128).
The Special Publication (SP) 800-128 provides updated guidance to help organizations securely configure (or “harden”), manage and monitor information systems. Hardened systems can help organizations reduce the attack surface and make it harder for attackers to exploit systems.
NIST introduces a new term dubbed Security-Focused Configuration Management (SecCM) as they describe in SP 800-128 abstract:
“The focus of this document is on implementation of the information system security aspects of configuration management, and as such the term security-focused configuration management (SecCM) is used to emphasize the concentration on information security. In addition to the fundamental concepts associated with SecCM, the process of applying SecCM practices to information systems is described. The goal of SecCM activities is to manage and monitor the configurations of information systems to achieve adequate security and minimize organizational risk while supporting the desired business functionality and services.”
Introducing SP 800-128
The latest SP 800-128 (PDF) includes implementation guidance for the Configuration Management family of controls as defined in NIST SP 800-53.
“Configuration management is an important process for establishing and maintaining secure system configurations, and provides important support for managing security risks in systems,” NIST stated.
SP 800-128 also includes SecCM fundamentals and the SecCM process (such as how to implement/monitor SecCM).
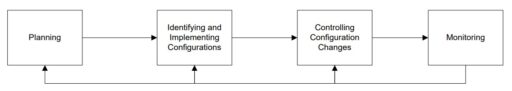
In this blog post, I have highlighted key points from the NIST SecCM process, that consists of four phases (also see Figure 1 below):
- Planning SecCM
- Identifying and implementing SecCM
- Controlling configuration changes
- Monitoring.
1) Planning SecCM
The Planning phase of SecCM consists of developing policies and procedures for SecCM, Configuration Control Boards (CCBs), secure hardening baseline configurations and monitoring to name a few.
To add, organizations need to establish metrics for systems that meet SecCM hardening baselines.
2) Identifying and implementing SecCM
In the second phase, organizations will need to develop a baseline configuration that represents a “secure state” such as secure configurations, software patch levels and how controls are implemented and documented.
The Center of Internet Security (CIS) has published quite a number of baseline configurations or “benchmarks” for over 140 different technology platforms, such as Windows, Linux systems and many others.
Organizations will then need to approve and implement the SecCM baselines. To add, automation can help organizations more uniformly apply baseline configurations across their systems.
Tool examples include Microsoft’s System Center Configuration Manager (SCCM), Puppet, Chef or Ansible, just to name a few.
3) Controlling configuration changes
As part of good change management practice, changes should be formally reviewed, tested, analyzed for security impact and approved prior to implementation. Access to systems should also be tightly controlled, such as using least privilege and role-based access control.
NIST also recommends organizations use Configuration Control Boards (CCBs) to formally review and approve new changes to information systems and baselines.
4) Monitoring
Organizations should use automated tools to more efficiently monitor and identify changes to approved baseline configurations. Once unauthorized changes are identified, remediation actions should then be implemented.
Some examples of good tools to help identify changes to hardening baselines include Rapid7’s InsightVM and Tenable, not to mention Chef and SCCM (as previously noted).
Finally, NIST provides a number of useful Appendices and templates in SP-800-128 such as secure configuration best practices, CCB charter sample and security impact analysis template to name a few.
This latest revision to SP-800-128 supercedes the last publication NIST provided in August of 2011.
