
The National Security Agency (NSA) has released guidelines to help organizations mitigate cloud vulnerabilities. The NSA document includes four classes of vulnerabilities at most risk to threat actors.
According to the latest publication “Mitigating Cloud Vulnerabilities,” NSA says the four main categories of cloud vulnerabilities include misconfiguration, poor access control, shared tenancy vulnerabilities and supply chain vulnerabilities.
The NSA provides descriptions of each of the vulnerabilities, as well as effective mitigations to help organizations lock down their cloud environments.
In addition, the guidelines offer Cloud Components and Cloud Threat Actors sections, to help readers gain a good perspective on security principles.
Cloud Components
Most Cloud Service Providers (CSPs) include four standard cloud architectural services: Identity and Access Management (IdAM), Compute (e.g., virtualization, containers), Networking (e.g., isolation, software defined networking, and Storage (e.g., Objects, Blocks, and Database Records).
In addition, cloud encryption and key management (KM) form a critical component for protecting data in the cloud.
For instance, customers have multiple options such as using the CSP’s own encryption and KM services. These services can help reduce cost and development overhead to integrate with other cloud services.
Organizations can also generate their own keys used in encryption (such as Bring Your Own Key).
In addition, customers can use their own on-premise hardware security module (HSM) outside of the cloud. This option could minimize the impact of exposing encryption and KM to cloud administrators. Of course, this likely comes with a higher cost.
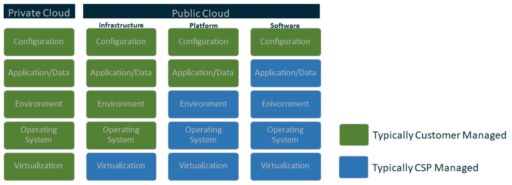
Cloud Shared Responsibilities is a critical cloud component. For instance, CSPs are responsible for securing the cloud infrastructure, as well as implementing logical controls to separate out customer data. Customers are typically responsible for access controls to systems and data, as well as patching their virtual operating systems.
The NSA has provided a diagram of cloud shared responsibility model (see Figure 1):
Cloud threat actors
Organizations should understand the different types of cloud threat actors. In some ways, the threat actors are similar to those for on-premise. For example, malicious CSP administrators and malicious customer cloud administrators can be a critical threat actor to an organization’s resources.
In addition, cyber criminals and state sponsored actors pose a major threat to cloud resources, similar to on-premise environments.
To add, untrained or neglectful cloud admins could also expose sensitive data.
Cloud vulnerabilities and mitigations
The NSA has provided descriptions of four cloud vulnerability classes, along with some effective mitigations.
Misconfiguration
According to the NSA, “misconfiguration of cloud resources remains the most prevalent cloud vulnerability and can be exploited to access cloud data and services.”
To add, misconfigurations often are the result of policy mistakes or misunderstanding shared responsibility. As a result, the impact can result in denial of service attacks, sensitive data loss or account compromise.
The guidelines provide three examples the last three years of how misconfiguration resulted in sensitive cloud data exposure to the public.
To help mitigate misconfigurations, organizations can implement “least privilege” and “defense in depth” controls.
Examples of least privilege controls can include:
- Establish mission-justified roles for admins and also to prevent users from sharing data publicly.
- Consider “Zero Trust” model to limit access to and between cloud resources.
- Implement hardening policies to ensure resource default as private.
- Use automated tools to audit access logs and identify overly-exposed data.
- Restrict senstive data to only approved cloud storage.
- Implement Data Loss Prevention to enforce data restrictions and monitor for data loss.
Defense-in-depth controls should include, for example:
- Enforce encryption of data at rest and in transit with strong encryption algorithms.
- Implement and monitor properly configured properly configured key management systems.
- Adhere to cloud standards (e.g., CSP guidance, Center for Internet Security Benchmarks).
- Use and control virtual machine images and hardening baselines.
- Control and audit cloud service policies and IdAM changes.
- Ensure that logging is enabled at all levels.
- Enable endpoint controls (e.g., anti-malware and EDR).
- Prevent abuse of privileged accounts (e.g., separation of duties).
- Automated continuous monitoring for configuration changes and security events.
- Identify and eliminate shadow IT.
Last, organizations should take advantage of built-in CSP services and tools to help with migrations to the cloud, such as Infrastructure-as-code (IaC) to help prevent misconfigurations.
Poor access control
According to the NSA, poor access control typically happens when organizations use weak authentication and authorization methods.
This also occurs when hackers can exploit vulnerabilities to bypass such methods. For example, using simple login account and password in lieu of multi-factor authentication (MFA).
Additionally, hackers could exploit weak authentication protocols (such as TLS 1.0/1.2, SSL versions) to elevate privileges and compromise cloud resources.
Examples of strong access controls include:
- Use multi-factor authentication for access to cloud resources and password resets.
- Disable protocols that use weak authentication.
- Implement automated tools to audit access logs.
- Use Zero Trust model.
- Use CSP-managed authentication between virtual machines or Active Directory.
- Do not include API keys in software version control systems (to prevent leakage).
Shared tenancy vulnerabilities
Shared tenancy vulnerabilities can exist in cloud hypervisors or container platforms. As a result, bad actors could exploit these vulnerabilities and cause severe impact.
Although, exploitation of hypervisor vulnerabilities are more difficult and expensive, organizations should still be aware of these threats.
NSA provided two examples of how researchers were able to demonstrate hypervisor breakout attacks.
In another more recent example, an attacker was able to find a vulnerability in a container platform. As a result, the actor could then overwrite the container runtime and then gain access to other containers running on the same platform.
Mitigations to prevent shared tenancy vulnerabilities include:
- Enforce encryption of data at rest and in transit with strong encryption algorithms.
- Implement and monitor properly configured properly configured key management systems.
- Use accredited cloud services (where applicable)
- Use dedicated bare metal instances or whole-units (for isolating more sensitive workloads)
- Leverage virtualization for isolation instead of containerization (for sensitive workloads).
Finally, organizations can leverage the National Information Assurance Partnership (NIAP) Protection Profiles (PPs) and NIAP Server Virtualization PP to help in consistent evaluation of critical cloud components.
Supply chain vulnerabilities
In the final vulnerability category, Supply Chain vulnerabilities in the cloud can include the presence of intentional backdoors embedded in hardware and software.
Additionally, inside attackers or agents can insert themselves into the cloud supply chain. As a result, a supplier, administrator or developer could compromise cloud environments as part of nation state attack.
Examples of these threats include the ShadowHammer attack in 2018. In these attacks, cybercriminals hijacked ASUS Live Update and downloaded a back-doored version to thousands of ASUS PCs.
In another supply chain attack, researchers discovered last December malicious Python Package Index (PyPI) libraries designed to steal credentials from developer systems that installed them.
Administrators can implement these strong controls to defend against supply chain attacks:
- Make sure development and migration contracts stipulate adherence to internal standards or equivalent procedures for addressing supply chain risks.
- Control the selection of virtual machine images to prevent the use of untrustworthy third party products, such as malicious cloud marketplace offerings.
- Review vendor-specific countermeasures with your CSP to drive risk decisions.
Similar to the other vulnerability mitigations, organizations should also enforce strong data encryption and key management controls.
Conclusion
In conclusion, the NSA says organizations should carefully consider cloud threats and vulnerabilities during procurement process and an ongoing basis.
Cloud platforms, such as AWS, Azure or Google Cloud, can provide numerous advantages over traditional onpremise technologies. Clouds can help organizations automate IT and security processs, such as threat and incident response.
With that said, cloud security is still a shared responsibility organizations share with CSPs.
“Security in the cloud is a constant process and customers should continually monitor their cloud resources and work to improve their security posture,” the NSA concluded.
