Security experts from Microsoft have revealed threat actors are increasingly using web shell attacks in their campaigns. Microsoft’s investigation revealed actors such as ZINC, KRYPTON, and GALLIUM, exploit known vulnerabilities to implant web shells on internet-facing web servers.
A web shell is a piece of malicious code used by attackers to implant on web servers and gain foothold for further compromise.
Web shells are often written in common web development programming languages, such as ASP, PHP and JSP. For example, one of the most widely used web shells, China Chopper, is written in JSP.
To add, attackers will often try to hide web shells within files in order to blend in with other legitimate web server files. Examples include: index.aspx, fonts.aspx, default.php, function.php, help.js, write.jsp, and others.
As part of a recent investigation, Microsoft’s Detection and Response Team (DART) responded to an incident at one of their customers in the public sector.
The DART team then discovered bad actors “uploaded a web shell in multiple folders on the web server,” which then led to “the subsequent compromise of service accounts and domain admin accounts.”
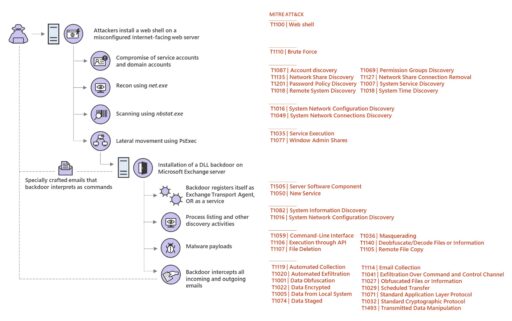
As a result, the attackers could then run reconnaissance using net.exe and also scan for additional target systems using nbstat.exe. They could then use PsExec to move laterally. PsExec is a client-less tool used to execute processes on other systems, with full interactivity for console applications.
Microsoft also provided a sample web shell attack chain (Figure 1):
Microsoft also warned that bad actors will typically exploit unpatched web server vulnerabilities, such as CVE-2019-0604 or CVE-2019-16759. The latter was used in VBulletin zero-day exploits in the wild.
Recommended Mitigations
Microsoft also offered good guidance on how organizations can harden against web shell attacks. Examples include:
- Identify and patch vulnerabilities as soon as updates are available.
- Audit and review logs from web servers frequently.
- Prevent command-and-control communications by using intrusion detection systems, as well as host-based and network-based firewalls.
- Restrict perimeter access to unnecessary services/ports via proxy and firewall.
Microsoft also recommended organizations educate their end users about preventing malware infections. Organizations should also limit use of accounts with local or domain privileges.