
Several years ago, the Federal Trade Commission (FTC) released a good video that is still highly relevent today. The video explains how companies can leverage NIST’s Cybersecurity Framework to greatly improve security in their organization. In this article, we highlight the five key tenants from the framework and how they could have possibly prevented FTC action and penalties.
The video helps describe how the NIST Cybersecurity Framework aligns with the FTC’s work on data security. The FTC also highlights how organizations can use the Framework and the FTC’s “Start with Security” guidance.
The Cybersecurity Framework
First, a brief overview of the Cybersecurity Framework is outlined in Figure 1 below. The framework is composed of a “Framework Core” as defined by the National Institute of Standards and Technology (NIST) as a “set of activities to achieve specific cybersecurity outcomes, and reference examples of guidance on how to achieve those outcomes.”
The core is nicely organized into five functions or basic cybersecurity activities — 1) Identify, 2) Protect, 3) Detect, 4) Respond and 5) Recover. These functions can be used to organize and group together information that management can use to implement security safeguards, measure progress and prioritize security efforts.
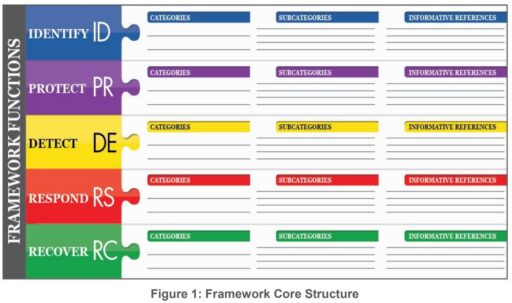
Each of the functions are then divided into categories to define more specific security practices and capabilities (e.g., asset management, access control).
See NIST Cybersecurity Framework Table 1 for Function and Categories as illustrated below:
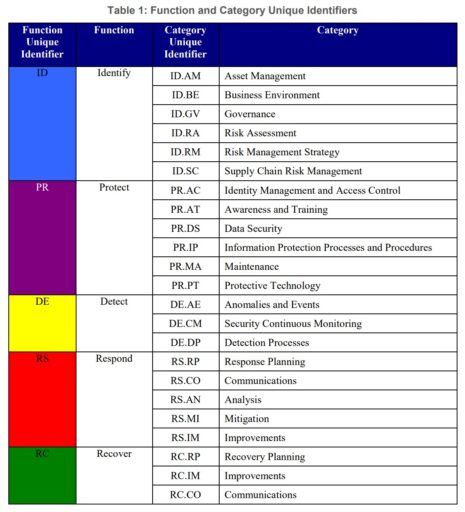
Subcategories further describe more detailed or technical security controls that are needed to meet objectives within each category. To add, Informative references can also be used to refer to industry standards and best practices (e.g., NIST “Special Publications” or ISO 27001 standards).
The FTC emphasizes that the Cybersecurity Framework is not a “one-sized-fits-all” approach to managing cybersecurity risks and is certainly not a checklist. Rather, businesses should use the framework as best practices and “common language” to consider when building a cybersecurity program.
In addition, it is noteworthy that the Framework is closely related to the FTC’s work on data security (see video). For instance, the FTC has undertaken substantial efforts over the past decade to promote data security protections such as:
- Civil law enforcement (see FTC Act Section 5: “Unfair or Deceptive Acts or Practices” as enforcement tool)
- Business and consumer education policies and
- Recommendations to congress to enact new legislation.
So, here are five (5) important lessons learned from FTC’s nearly 60 case settlements and how implemented Cybersecurity Framework best practices could have helped prevent a negative outcome.
1) Identify
Identify: “Develop the organization’s understanding to manage cybersecurity risk to systems, assets, data and capabilities.”
In two separate complaints against HTC America, Inc. and TRENDnet, Inc., the FTC alleged that the two companies “did not have a process for receiving, addressing, or monitoring reports about security vulnerabilities.”
The HTC settlement was the FTC’s first against a mobile device manufacturer. The settlement also highlighted multiple security practice deficiencies to include: inadequate security and privacy training, lack of testing/auditing of the software on its mobile devices for potential security vulnerabilities, need for secure programming practices, and gap in process for receiving and addressing vulnerability reports from third parties.
Similarly, TRENDnet had faulty software that left them “open to online viewing, and in some instances listening, by anyone with the cameras’ Internet address.” As also highlighted in the Cybersecurity framework, the FTC recommended a comprehensive security program to address security risks, patches to address vulnerabilities and also need for third party security assessments.
2) Protect
Protect: “Develop and implement the appropriate safeguards to ensure delivery of critical infrastructure services.”
The FTC settled two similar cases against Accretive Health, Inc. and Cbr Systems, Inc. due to the manner in which an employee laptop and portable storage, respectively, were poorly handled and led to the theft and exposure of personal information.
As highlighted in the Framework’s “Protect” guidance, data must be transported securely and use strong encryption controls. Examples include laptop whole disk encryption or USB password protected (and encrypted) USB drives. Each of these controls can protect the data in the event devices are lost or stolen.
In addition, organizations need to implement strong vulnerability management program. Equifax failed to patch an Apache Struts vulnerability CVE-2017-5638. This failure in protection and response controls (also see section 4 below) led to one of the biggest data breaches in history. As a result, Equifax settled a massive fine with the FTC last year.
See NIST Table 2 (Framework Core) for details on these and many other protective controls.
3) Detect
Detect: “Develop and implement the appropriate activities to identify the occurrence of cybersecurity events.”
The FTC alleged that Franklin’s Budget Car Sales, Inc. allowed the installation of Peer-to-Peer (P2P) software on their network. The incident led to sensitive data being uploaded to P2P network and the compromise of 95,000 consumer records.
These reported deficiencies didn’t align with the Framework’s “Detect” guidance. For instance, the need for monitoring networks for potential security events or for unauthorized devices, software or user connectivity.
4) Respond
Respond: “Develop and implement the appropriate activities to take action regarding a detected cybersecurity event.”
In February 2016, the FTC settled a case with Taiwan-based computer hardware maker ASUSTeK Computer, Inc.. The settlement came after ASUS failed to fix a number of critical security flaws in its routers. The issue also put hundreds of thousands of home networks and consumers at risk.
The complaint also included charges against the ASUS cloud services that led to thousands of cloud-connected storage devices to be compromised and exposed personal data to the internet.
One of the important points to the case, FTC alleges, is the failure of ASUS to notify their customers of the risk of unpatched router vulnerabilities nor did the company address the security flaws in a timely manner.
5) Recover
Recover: “Develop and implement the appropriate activities to maintain plans for resilience and to restore capabilities or services that were impaired due to a cybersecurity event.”
In the final example, the FTC settled a case with Oracle. The FTC alleged the company had deceived consumers about the security update process to its Java Platform, Standard Edition software (Java SE).
In short, Oracle failed to notify consumers that the Java SE update only addressed the most recent version of Java, but did not remove the earlier versions. As most security practitioners know, hackers can craft malware to exploit older version of Java vulnerabilities. So it is important to remove legacy/unused software and ensure all software is up to date.
Based on these lessons learned and settlement with the FTC, Oracle since changed its practices. For instance, Oracle now notifies consumers during the Java SE update process if they have outdated versions of the software on their computer (and the risks of not removing older software). The company also gives consumers an option to uninstall the software.
Conclusion
Each of these five functional areas of the Cybersecurity framework can help organizations with simple, yet powerful security best practices.
In July 2019, Equifax Inc. agreed to sign a settlement with the FTC to pay at least $575 million, and potentially up to $700 million, related to the massive data breach in 2017 that impacted nearly 147 million people.
These FTC law enforcement cases and settlements highlight some good examples of controls needed to help reduce similar incidents and costly fines in your organization.
You can download the full Cybersecurity Framework 1.1 framework published by NIST here.
Updated April 5, 2020: this article was originally posted on April 2, 2017 and updated to include latest Cybersecurity Framework version, incidents and updated content.
