
TrickBot recently replaced one of its propagation modules “mworm” with new module named “nworm.” The updated module can exploit vulnerable domain controllers (DCs) and evade detection by running in memory.
TrickBot traces its roots back to 2016 as a modular banking trojan designed to steal information and distribute other malware to infected systems.
Security experts from Palo Alto Networks Unit 42 team discovered the new artifact named “nworm” on an infected Windows 7 client.
One of the key differences with previous modules is nworm is not persistent. In other words, the malware runs from memory on an infected DC and disappears after reboot. This differs from mworm that is persistent and runs on an infected DC.
TrickBot propagation flow
The propagation flow first starts with a TrickBot-infected Windows system that will use nworm to exploit an SMB vulnerability on a vulnerable DC.
In addition, nworm will retrieve over the network a TrickBot executable file, in the form of an encrypted, encoded binary file.
The binary is then decoded and then runs on the victim DC’s memory, which leaves no files behind.
Unit 42 describes the propagation flow in Figure 1 below:
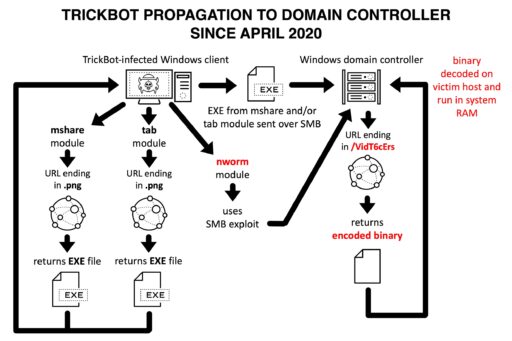
Furthermore, TrickBot uses two other modules called mshare and tab. These modules can retrieve a new TrickBot EXE via an HTTP URL or will send the TrickBot EXE over SMB traffic to the vulnerable DC.
Readers can check out Palo Alto Networks blog post for more details on the TrickBot module updates, history and indicators of compromise.
To reduce risk of TrickBot infections, organizations should keep their Windows systems up to date and run anti-malware solutions.
