
North Korea’s BeagleBoyz cybercriminals have launched an automated teller machine (ATM) cash-out scheme, known as FASTCash 2.0. Cyber experts from the U.S. government have detected the cyber activity over the past five years that led to nearly $2B in losses to financial institutions around the world.
The cyber experts warned these cyber attacks pose significant operational risk to Financial Services firms and reduces the integrity of the worldwide financial system.
In a joint technical alert, the Cybersecurity Security and Infrastructure Security Agency (CISA), the Department of the Treasury (Treasury), the Federal Bureau of Investigation (FBI) and U.S. Cyber Command released details on the North Korean BeagleBoyz threat. The report also included identified malware used in FASTCash campaign, along with indicators of compromise (IOCs).
“The BeagleBoyz’s bank robberies pose severe operational risk for individual firms beyond reputational harm and financial loss from theft and recovery costs,” CISA warned in the alert.
“The BeagleBoyz have attempted to steal nearly $2 billion since at least 2015, according to public estimates. Equally concerning, these malicious actors have manipulated and, at times, rendered inoperable, critical computer systems at banks and other financial institutions.”
Furthermore, the FBI said that the bad actors are using malware variants in conjunction with proxy servers to compromise and remain on victim networks in order to exploit other targets on the network.
For instance, the following malware variants were used and called out in the report:
FASTCash 2.0 update
In the latest update, the U.S. government experts explained that the BeagleBoyz “FASTCash” campaign became public in October of 2018, but has been active since 2016. Over past five years, BeagleBoyz has been targeting banks’ retail payment system infrastructure.
“Fraudulent ATM cash outs have affected upwards of 30 countries in a single incident. The conspirators have withdrawn cash from ATM machines operated by various unwitting banks in multiple countries, including in the United States,” CISA explained.
However, since October 2018, the FASTCash 2.0 campaign shifted to adding two new significant capabilities:
- FASTCash scheme now used against banks hosting their switch applications on Windows servers.
- FASTCash campaign now targets interbank payment processors.
“In October 2018, the U.S. Government identified malware used in the FASTCash scheme that has the capability to manipulate AIX servers running a bank’s switch application to intercept financial request messages and reply with fraudulent, but legitimate-looking, affirmative response messages to enable extensive ATM cash outs,” CISA noted.
The cyber experts also identified functionally equivalent malware targeting and running on Windows systems.
In addition, FASTCast malware was observed targeting at least two regional interbank payment processors (above and beyond switch applications hosted at individual banks).
CISA also provided a nice overview of the BeagleBoyz Bank Heist as highlighted in Figure 1 below:
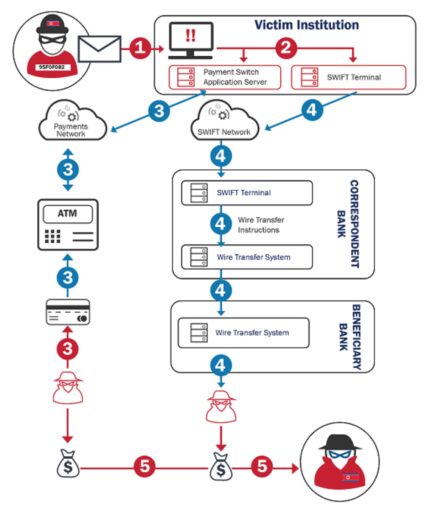
Malware execution
The report also highlights how BeagleBoyz exploits victim computers after compromising systems connected to a bank’s corporate network.
Some of the techniques the actors use include:
- Use command-line interfaces to interact with systems and execute other software (Command and Scripting Interpreter).
- Use scripts such as VBScript and PowerShell to speed up operational tasks to compromise systems and bypass monitoring mechanisms. These scripts can interact with the OS at API level in lieu of calling other programs.
- Phishing: Can rely on users opening malicious email attachments.
- Exploit vulnerabilities to execute code.
- Create or modify services in order to run executables, commands or scripts.
- Employ the Windows module loader to load Dynamic Link Libraries (DLLs) from arbitrary local paths or arbitrary Universal Naming Convention (UNC) network paths and execute arbitrary code on a system.
- Abuse the Windows API to execute arbitrary code on the victim’s system.
- Use a system’s graphical user interface (GUI) to search for information and execute files.
- Use the Task Scheduler to run programs at system startup or on a schedule for persistence, conduct remote execution for lateral movement, gain SYSTEM privileges for privilege escalation, or run a process under the context of a specified account.
- Abuse compiled Hypertext Markup Language (HTML) files (.chm) to conceal malicious code.
- Abuse Windows rundll32.exe to execute binaries, scripts, and Control Panel Item files (.CPL), as well as execute code via proxy to avoid triggering security monitoring tools.
- Exploit cron (Linux) and launchd (macOS) to create pre-scheduled and ongoing background jobs.
The BeagleBoyz actors also use malware, such as CROWDEDFLOUNDER and HOPLIGHT, to maintain remote access to bank networks and also interact with those systems.
“HOPLIGHT has the capability to create fraudulent Transport Layer Security (TLS) sessions to obfuscate command and control (C2) connections, making detection and tracking of the malware’s communications difficult,” the experts explained.
Furthermore, BeagleBoyz also use network proxy tunneling tools (e.g., VIVACIOUSGIFT, ELECTRICFISH) to tunnel communications from non-internet facing systems to internet-facing systems. Examples of those internal systems include ATM switch application servers or SWIFT terminals.
As a result, the actors can then use those proxy tunnel tools to tunnel protocols (such as RDP or SSH) out from the internal network.
Recommended mitigations
The report highlights many good mitigations to help minimize the FASTCash threat, such as:
- Segregate payment networks from rest of corporate networks.
- Use multi-factor authentication (MFA) to access sensitive environments.
- Prevent internet hosts (as well as unauthorized endpoints) from accessing the private network infrastructure servicing your payment switch application server.
- Use network firewalls to segregate environments.
- Encrypt data in transit.
- Monitor for anomalous behavior as part of layered security.
- Validate issuer responses to financial request messages and enforce Chip and PIN requirements for debit cards.
- Patch and keep software up to date.
- Maintain anti-virus and run personal host-based firewall.
- Disable file, printer sharing and any other unnecessary services.
- Do not add users to local administrators’ group (to limit ability to install software).
- Enforce a strong password policy and require regular password changes.
- Be wary of opening up email attachments.
- Restrict and monitor access to high risk or unfavorable websites.
- Be wary of using removable media.
- Scan all software downloaded from the internet before executing.
- Maintain situational awareness of the latest threats.
- Implement appropriate access control lists.
Readers of the report are also encouraged to contact CISA, the FBI or the Treasury Office of Cybersecurity and Critical Infrastructure Protection if you have any questions about the report or wish to report an incident related to this threat.
