
Security researchers from Guardicore discovered a sophisticated peer-to-peer (P2P) botnet dubbed FritzFrog has been actively breaching SSH servers since January 2020.
According to Guardicore, FritzFrog executes Golang-based worm malware that is multi-threaded and fileless. In other words, it assembles and executes payloads in-memory and leaves no trace on the infected victim’s system disk.
“FritzFrog has attempted to brute force and propagate to tens of millions of IP addresses of governmental offices, educational institutions, medical centers, banks and numerous telecom companies,” Guardicore warned in the blog post.
“Among those, it has successfully breached more than 500 servers, infecting well-known universities in the U.S. and Europe, and a railway company.”
Also, the malware authors appear to have built the malware from scratch hinting they likely are highly skilled software developers.
FritzFrog is highly unique in that it communicates with decentralized infrastructure instead of typical command and control (C2) infrastructure. For instance, it distributes control among all of its nodes with no single point of failure.
As a result, the nodes keep in constant communication with each other and keep the network up to date and alive over an encrypted channel.
Furthermore, FritzFrog appears to be more aggressive in its brute-force attacks and uses its own proprietary P2P protocol.
FritzFrog campaign
Guardicore first spotted FritzFrog campaign activity on January 9, 2020. Overall, the security firm’s global sensors detected 13K cyberattacks and 20 different versions of the FritzFrog malware binary.
After its victims are breached, FritzFrog runs a UPX-packed malware and instantly erases itself. It also runs under the names opconfig and nginx, to minimize detection and begins to listen on non-standard port 1234.
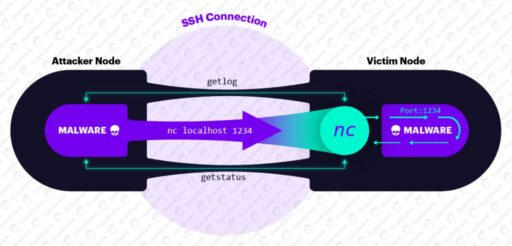
To further reduce suspicion, FritzFrog employs a creative technique according to Guardicore (also shown in Figure 1):
“The attacker connects to the victim over SSH and runs a netcat client on the victim’s machine, which in turn connects to the malware’s server. From this point on, any command sent over SSH will be used as netcat’s input, thus transmitted to the malware.”
Mitigations
For mitigations, Guardicore recommends organizations monitor for running processes (nginx, ifconfig or libexec) that no longer exist on the file system.
Also, pay attention to suspicious traffic over port 1234 and also 5555, the latter could indicate network traffic to the Monero pool.
Finally, organizations can implement process-based segmentation and also use strong passwords and public key authentication.
