
The National Security Agency (NSA) and the Federal Bureau of Investigation (FBI) have released a joint cybersecurity alert for a new Russian malware dubbed Drovorub.
According to the NSA and FBI cyber experts, Drovorub is likely linked to Russian advanced persistent threat (APT) actor.
The APT actor is identified as the Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS), military unit 26165.
Drovorub was previously undisclosed malware that runs on Linux systems and is part of cyber espionage operations performed by GTsSS. The group’s activity was also linked to other names such as Fancy Bear, APT28, Strontium, and others.
An excerpt from the cybersecurity advisory describes the Drovorub threat:
“Drovorub is a Linux malware toolset consisting of an implant coupled with a kernel module rootkit, a file transfer and port forwarding tool, and a Command and Control (C2) server. When deployed on a victim machine, the Drovorub implant (client) provides the capability for direct communications with actorcontrolled C2 infrastructure; file download and upload capabilities; execution of arbitrary commands as “root”; and port forwarding of network traffic to other hosts on the network.
Joint advisory from the NSA and FBI
In addition, the Drovorub compents and functions are also illustrated in the following Figure 1 and table (provided in the advisory):
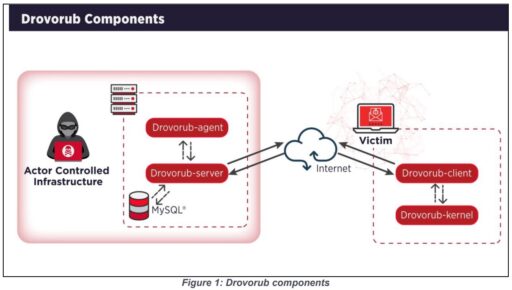
| Drovorub Component | Function |
| Drovorub-client | Implant |
| Drovorub-kernel module | Rootkit |
| Drovorub-agent | Port Forwarding and File Transfer Too |
| Drovorub-server | Command and Control (C2) Server |
Furthermore, the cybersecurity experts warn the Drovorub-kernel module makes it hard to detect on systems since it hides Drovorub artifacts from security monitoring and response tools.
Mitigations
To help mitigate against Drovorub, system admins should update Linux systems to Linux Kernel 3.7 or later in order for systems to enforce kernel signing.
In addition, the NSA and FBI also recommends organizations configure systems to load only modules with a valid signature. Thus, bad actors would have a much harder time introducing a malicious kernel module into the system.
Readers can check out the full advisory for many more technical details and figures on the Drovorub threat.
