
Microsoft has worked with telecommunications providers worldwide to take down TrickBot malware infrastructure.
TrickBot traces its roots back to 2016 as a modular banking trojan designed to steal information and distribute other malware to infected systems.
Bad actors typically delivered TrickBot via email campaigns based on current events (such as COVID-19) or financial incentives to trick users into opening up malicious file attachments (such as Word or Excel macro-enabled docs).
Over the past several years, TrickBot added detection evasion features and redirect victims to fake websites to steal banking credentials, just to name a few.
This June, researchers discovered TrickBot further added a propagation module with nworm to evade detection and target Active Directory domain controllers.
So it goes without saying, this is welcome news that the TrickBot threat and massive botnet has finally been taken down.
“As a result, operators will no longer be able to use this infrastructure to distribute the Trickbot malware or activate deployed payloads like ransomware,” Microsoft stated in a blog post Monday.
Microsoft also described various TrickBot campaigns in an infographic as illustrated in Figure A:
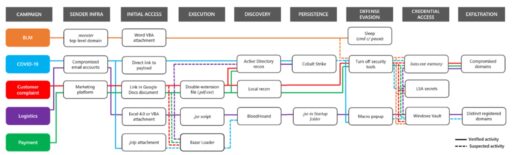
Furthermore, Microsoft added the takedown action will result in malware protections for a wide range of private and public organizations from TrickBot-based campaigns.
The tech giant added organizations should continue to be vigilant against other “commodity threats” like TrickBot, that allow cybercriminals of all skillsets to take advantage of.
Related Articles
- TrickBot trojan updates propagation module with nworm to evade detection
- Trickbot and Shellbot malware threats
- 2020 Threat Landscape Report reveals new themes and evolving threats
- Trickbot used to redirect users to fake bank website
- Security experts see sharp increase in the Emotet botnet activity
- FBI: Beware of banking trojans and fake mobile banking apps
- Emotet malware campaign warning
