
Microsoft shared new insights into the Solarigate malware, the compromised DLL file behind the SolarWinds software supply chain attacks.
The analysis comes on the heals of recent compromise of SolarWinds software by threat actors that led to cyberattack against SolarWinds customers in critical infrastructure, government and private sector organizations.
Solarigate, also known as Sunburst backdoor, consists of a compromised SolarWinds Orion Platform DLL and key component of SolarWinds software. The DLL file, SolarWinds.Orion.Core.BusinessLayer.dll, is a digitally-signed component of the Orion software framework.
According to Microsoft, the SolarWinds threat actors inserted a ‘few benign-looking lines’ of malicious code into the DLL:
“The discreet malicious codes inserted into the DLL called a backdoor composed of almost 4,000 lines of code that allowed the threat actor behind the attack to operate unfettered in compromised networks.“
Moreover, the actors likely infiltrated SolarWind’s software development cycle or distribution pipeline as far back as October, 2019. This is likely the reason the hackers were able to digitally sign the DLL files.
As a consequence, the digitally signed file can run privileged commands and go undetected by SolarWinds customers.
Microsoft further provided a high level diagram on the Solarigate malware infection chain used in the SolarWinds attack (see Figure 1):
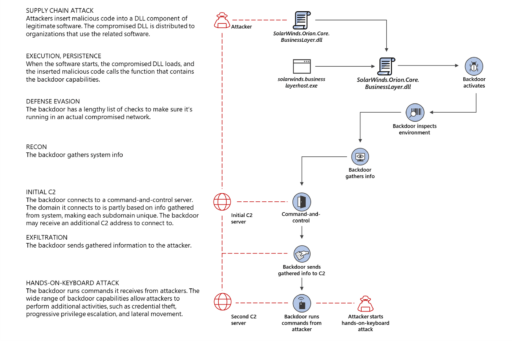
Readers can check out Microsoft’s report for more details on the poisoned code library and how the SolarWinds supply chain attack all started.
Also, check out previous articles on the SolarWinds cyberattacks in related articles below.
Related Articles
- CISA: Threat actors behind SolarWinds hack pose ‘grave risk’ (updated)
- Global active exploits against SolarWinds via Sunburst backdoor
- Threat actors targeting COVID-19 vaccine cold chain
- Cyberattacks against machine learning systems and the new Adversarial ML Threat Matrix
- Operation ShadowHammer hijacks ASUS Live Update to install backdoor
- CCleaner application backdoor
- Sodin ransomware spreads through MSPs
