
The National Security Agency (NSA) has issued new guidance to eliminate obsolete Transport Layer Security (TLS) protocol configurations (such as TLS 1.0, TLS 1.1, SSLv2, SSLv3 and weak ciphers).
The NSA highly recommends organizations replace their obsolete protocol configurations with strong encryption and authentication in order to protect all sensitive information.
“Over time, new attacks against Transport Layer Security (TLS) and the algorithms it uses have been discovered. Network connections employing obsolete protocols are at an elevated risk of exploitation by adversaries,” the NSA writes in the new guidelines CSI sheet on Eliminating Obsolete TLS Protocol Configurations.
Background
Sensitive data (such as personal data, login credentials, etc.) requires strong protected transmissions over a secure private communication channel, such as between a client and server.
TLS and Secure Sockets Layer (SSL) were originally developed as secure protocols between client/server using encryption and authentication. TLS also provides confidentiality, integrity and authenticity protections for data in transit over the network.
However, many organizations have not been able to keep their TLS configurations up to date.
“Nation-state and sufficiently resourced actors are able to exploit these weak communications,” NSA warned.
As a result, the NSA has provided updated guidance on obsolete TLS versions, weak ciphers, and key exchange mechanisms. In addition, the cyber experts have added detection and mitigation strategies.
Obsolete TLS versions
TLS protocol versions become obsolete over time and pose vulnerabilities if they are not removed or upgraded. The NSA recommends systems run only TLS 1.2 or TLS 1.3.
Furthermore, organizations should remove the following obsolete protocols: SSL 2.0, SSL 3.0, TLS 1.0 and TLS 1.1.
See NIST SP 800-52 Revision 2 Appendix F for related requirements for good guidance for supported TLS versions.
Obsolete cipher suites
As part of TLS 1.2 and TLS 1.3 configurations, NSA further recommends that organizations only use approved cryptographic algorithms as noted in Commercial National Security Algorithms.
TLS 1.2 configurations refer to the term “cipher suites,” which is the the negotiated and approved set of cryptographic algorithms for the TLS transmission. Weak or obsolete cryptographic cipher suites should be removed as they pose vulnerabilities that can be exploited by bad actors.
For example, weak cipher suites include NULL, RC2, RC4, DES, IDEA and TDES/3DES. TLS 1.3 does remove these cipher suites. However, some implementations that use both TLS 1.2 and 1.3 should be checked to make sure weak ciphers are removed.
Moreover, readers can check out NIST SP 800-52 Revision 2 (see section 3.3) for more details on recommended cipher suites. Appendix A also has a nice breakdown of often used acronyms used throughout the document.
Obsolete key exchange mechanisms
According to the NSA, cipher suites that use weak key exchange mechanisms (such as EXPORT or ANON) should not be used. An attacker could exploit key exchange mechanisms that use weak keys.
“NSA recommends RSA key transport and ephemeral DH (DHE) or ECDH (ECDHE) mechanisms, with RSA or DHE key exchange using at least 3072-bit keys and ECDHE key exchanges using the secp384r1 elliptic curve. For RSA key transport and DH/DHE key exchange, keys less than 2048 bits should not be used, and ECDH/ECDHE using custom curves should not be used,” NSA further explained in the paper.
Readers can again refer to NIST SP 800-52 Revision 2 for more details on recommended key exchange mechanisms.
Detection and mitigation
Finally, the NSA provides a summary of recommendations to both detect and mitigate obsolete TLS versions running on systems.
For instance, administrators should apply these three NSA detection strategies:
- Identify clients offering and servers negotiating obsolete TLS versions (such as SSL 2.0, SSL 3.0, TLS 1.0, TLS 1.1) via traffic analysis. If detected, analysts should remove them.
- For sessions using TLS 1.2, analysts should identify and remediate devices using obsolete cipher suites. They should then update the configurations on clients and servers to remove weak ciphers. CNSA compliant configurations should also be implemented.
- For sessions using TLS 1.2 or TLS 1.3 and recommended cipher suites, analysts should identify and remediate devices using weak key exchange methods.
Moreover, the guidelines summarize some sound mitigation to help eliminate TLS-related weaknesses and vulnerabilities, as outlined in Table 1 and 2 below:
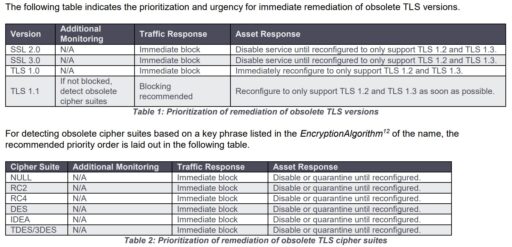
Analysts should prioritize and block as soon as possible much older protocols (such as SSL 2.0 and 3.0). They should also reconfigure systems that run TLS 1.0 and 1.1 to support TLS 1.2 and 1.3 as soon as possible.
In summary, organizations and analysts are strongly encouraged to use these new guidelines to help in their cause to eliminate weak TLS protocols, cipher suites and TLS implementations.
