
A new Pro-Ocean cryptojacking malware targets popular cloud applications including ApacheMQ, Oracle Weblogic and Redis. The malware contains four modules that execute to hide, mine cryptocurrency, watchdog and infect systems.
Palo Alto Network’s Unit 42 researchers discovered Pro-Ocean and tied the malware back to cyber gang Rocke Group.
“We previously saw simpler attacks by the Rocke Group, but it seems this group presents an ongoing, growing threat. This cloud-targeted malware is not something ordinary since it has worm and rootkit capabilities. We can assume that the growing trend of sophisticated attacks on the cloud will continue,” the Unit 42 researchers warned in the report.
The security experts further confirmed that Pro-Ocean is written in Go and each of the four modules consist of files written in multiple languages (C, Python or Bash) and a Bash script that executes it.
4 main modules
According to the Unit 42 report, Pro-Ocean consists of four main modules that get executed in order (see Figure A):
- Rootkit module
- Mining module
- Watchdog module
- Infection module
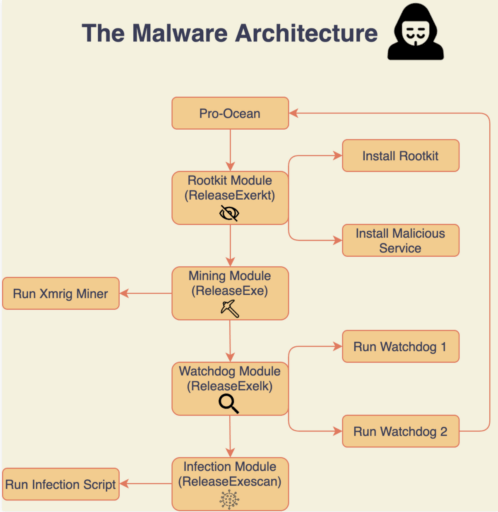
The Rootkit module (i.e.,ReleaseExerkt) first installs a rootkit and malicious service.
“The hiding module is responsible for concealing Pro-Ocean’s malicious activity. It uses a native Linux feature, LD_PRELOAD. LD_PRELOAD forces binaries to load specific libraries before others, allowing the preloaded libraries to override any function from any library,” Unit 42 described in the blog post.
Moreover, the mining module (ReleaseExe) then executes to run an Xmrig miner. Next in the sequence, Pro-Ocean executes the Watchdog module (i.e., ReleaseExelk) to run two Watchdog processes. The watchdog processes are designed to detect processes that use more than 30% of CPU (and kills it), as well as monitor the malware to make sure it is constantly running.
The final infection module runs an infection script that has worm-like capabilities to target vulnerabilities as described in the next section.
Targeted vulnerabilities
The Unit 42 security team found that Pro-Ocean targets multiple vulnerabilities including an Apache ActiveMQ (CVE-2016-3088) and Oracle WebLogic (CVE-2017-10271) vulnerability. The malware also targets unsecured Redis instances.
Once the vulnerabilities are exploited, the Python script will then send a payload used to download from a malicious HTTP server an installation script with multiple nefarious purposes. For example, the script can attempt to remove other types of malware, such as Luoxk, BillGates, XMRig and Hashfish before the malware installs.
Moreover, the installation script may disable the iptables firewall in order to allow the malware full internet access. The script can also search for SSH keys in an attempt to use them and infect new systems.
Readers should note that the WebLogic vulnerability CVE-2017-10271 was one of the “top 20” vulnerabilities most under attack back in late 2019. This vulnerability was patched in February 2018 and has since been used by attackers to deliver Monero miners.
Finally, Imperva security researchers discovered 72,000 internet-exposed Redis servers after scanning the internet in mid-2018.
Related Articles
- The top 20 vulnerabilities to patch now (that are most under attack)
- Internet exposed Redis servers
- RedisWannaMine Unveiled
- Oracle vulnerability exploited to deliver dual Monero miners
- NSA: Guidance to mitigate cloud vulnerabilities
- FireEye publishes Microsoft 365 tools and hardening strategies to defend against SolarWinds attackers
- FBI issues Flash Alert on Netwalker ransomware
