
The National Security Agency (NSA) has released new guidelines on the Zero Trust Security Model, a coordinated system management strategy that removes implicit trust in any one system or service and assumes breaches will or have already occurred.
The NSA also provided multiple good examples of Zero Trust controls, three that we reveal in this article.
First, the NSA describes the Zero Trust Security Model in the new information security cheat sheet:
The Zero Trust security model assumes that a breach is inevitable or has likely already occurred, so it constantly limits access to only what is needed and looks for anomalous or malicious activity. Zero Trust embeds comprehensive security monitoring; granular risk-based access controls; and system security automation in a coordinated manner throughout all
aspects of the infrastructure in order to focus on protecting critical assets (data) in real-time within a dynamic threat environment. This data-centric security model allows the concept of least-privileged access to be applied for every access decision, allowing or denying access to resources based on the combination of several contextual factors.
The guidelines not only describes the benefits of the Zero Trust Security Model, but also the challenges enterprises may face during implementation.
Guiding Principles of Zero Trust
The Zero Trust model encompasses these basic guiding principles, according to the NSA:
- Never trust, always verify
- Assume breach
- Verify explicitly.
Moreover, when designing Zero Trust architecture, enterprises must first look to define what is most valuable for the company to protect, to include the critical data, application, assets and services (DAAS).
Examples of DAAS include:
- Data: Payment card information (PCI), protected health information (PHI), sensitive personal information (SPI) or intellectual property.
- Applications: commercial-off-the-shelf (COTS) or custom developed software.
- Assets: customer database or web systems, point-of-sale terminals, medical devices or Internet of Things (IoT) devices.
- Services: Active Directory, DNS and configuration management tools.
As part of the architecture, organizations should “architect from the inside out,” by locking down systems and securing all access paths to your critical DAAS via access control policies and least privilege. Moreover, security teams will need to inspect and log all traffic to detect and act on suspicious activity.
To illustrate these principles, the NSA has provided several good examples of how the Zero Trust model can be used to thwart common cybersecurity threats. We have highlighted three of those examples and also added some related Zero Trust technical solutions organizations can consider as well.
1) Compromised user credentials
In the first example, a malicious actor compromises a user’s credentials and then seeks to access internal systems via an unauthorized device. An attacker could attempt this via remote access or by joining a rogue device to the victim’s wireless network.
To combat this threat, Zero Trust controls can deny access to the rogue device via authentication and authorization checks. Moreover, organizations should force strong authentication for users and devices.
For example, multi-factor authentication (MFA) requires an additional one time password or token to be entered to gain access to systems/services, thus making it more difficult for attackers to gain access if they steal a user’s password.
MFA solutions include those offered by Okta, Google Authenticator, Microsoft Authenticator and many others.
In addition, enterprises can implement “network access control” (NAC), such as Aruba’s Clearpass or Cisco’s Identity Services Engine. These NAC solutions can block network access to any device that does not meet certain “health checks” (such as approved SSL certificate, authorized user ID, Anti-virus version and patch levels, to name a few).
2) Moving laterally
In another good example, the NSA describes when a remote actor or even insider gains unauthorized access to a device internally and then moves laterally within the network. In legacy environments, an attacker could leverage this access to further pivot inside the network to compromise other systems or steal sensitive data.
Of course, Zero Trust always assumes a user and device is already untrusted or malicious until proven otherwise.
To limit the damage in this example, Zero Trust recommends enterprises segment their network to limit lateral movement. Moreover, access to data can further be limited to data via security policy, user role and even device attributes.
The NSA includes several examples where Zero Trust environments could prevent exploitation attempts, as illustrated in Figure 1 below.
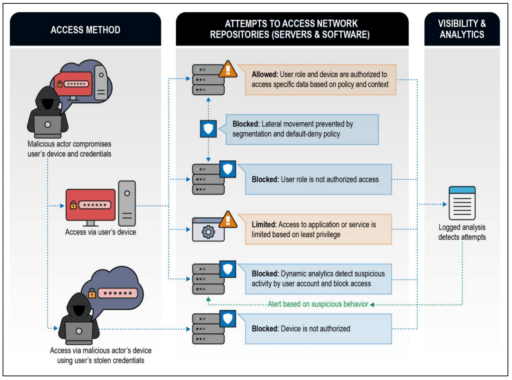
Furthermore, organizations should segregate their networks and systems into “security zones” such as DMZ, production, payment card, development and corporate networks, just to name a few. Each of the zones would include grouping of assets or systems based on data sensitivity and controls needed for data protection. In addition, firewalls can restrict network/data flows between zones and be enforced via firewall rules.
An example of a Zero Trust technical solution is Palo Alto Networks next generation firewalls. These network devices can offer not just network-level firewall protection, but also application-based policy enforcement (App-ID), intrusion detection protection (IPS), user authentication and network application traffic logging, just to name a few.
Moreover, the company also offers virtual appliances that can be used to better segregate cloud environment networks, such as Amazon Web Services, as well.
3) Compromised supply chain
By now, many organizations are already familiar with the recent SolarWinds supply chain attack. In this example, malicious actors embedded malicious code in SolarWinds Orion Platform software used by thousands of government and corporate customers.
Since the software was “trusted” internally, it could then be used to compromise other internal corporate systems and steal data.
In the Zero Trust model, however, a “deny-by-default” security policy should be implemented, whereby any compromised device would be blocked from communicating to outside/remote addresses used for command and control. In addition, organizations would use network monitoring to detect and policies (such as IPS or access policies) to block attempts to move laterally.
As mentioned in previous section, organizations should implement network segregation and firewall rule policies to only allow authorized requests from devices/applications.
Need for a more secure mission
The NSA reminds organizations of the need for a “more secure mission,” that also requires the full buy-in to the Zero Trust model by the organization – to include leadership, administrators and users.
Moreover, it is essential that Zero Trust capabilities are scalable and embodies robust infrastructure for continuously “making, enforcing and logging” access control decisions.
“The ever-increasing complexity of network environments and the ability of adversaries to compromise them requires a change in defensive focus. The Zero Trust mindset focuses on securing critical data and access paths by eliminating trust as much as possible, coupled with verifying and regularly re-verifying every allowed access,” the NSA explained.
