A banking trojan dubbed “Bizarro” that originated from Brazil has now targeted customers of 70 banks in Europe and South America.
According to Kaspersky researchers, Bizarro attempts to steal credentials from banking customers while “using affiliates or recruiting money mules to operationalize their attacks, cashing out or simply to helping with transfers.”
“Bizarro has x64 modules and is able to trick users into entering two-factor authentication codes in fake pop-ups. It may also use social engineering to convince victims to download a smartphone app,” Kaspersky wrote in a blog post.
The cybercriminal group behind Bizarro leverages servers hosted on compromised WordPress servers, as well as hacked Azure and AWS-host systems to store the malware and collect telemetry.
Moreover, the Bizarro malware is distributed via MSI package and is downloaded from a compromised site after victims click on links embedded in spam emails.
Bizarro backdoor
According to Kaspersky, the backdoor is the core component of Bizarro:
“It contains more than 100 commands and allows the attackers to steal online banking account credentials. Most of the commands are used to display fake pop-up messages to users. The core component of the backdoor doesn’t start until Bizarro detects a connection to one of the hardcoded online banking systems.”
Kaspersky added the Bizarro accomplished this objective by enumerating all the windows, thus collecting their names. Once a window name matches one of the hardcoded strings, the backdoor then continues starting up.
Attack flow
With these commands, Bizarro actors can stage attacks such as described by Kaspersky in the following diagram:
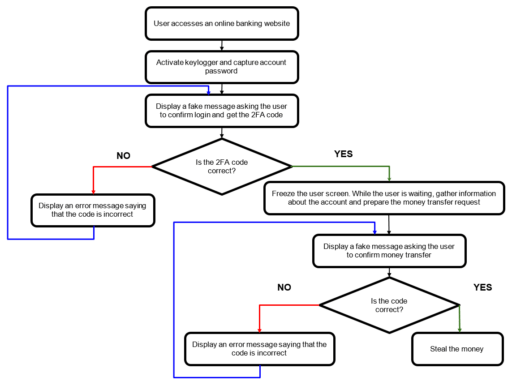
Readers can check out the full report to learn more about Bizarro commands and methods used in the attacks.
Related Articles
- New version of CRAT remote access trojan targets endpoints
- FBI: Beware of banking trojans and fake mobile banking apps
- TrickBot trojan updates propagation module with nworm to evade detection
- LokiBot trojan disguised as popular game launcher
- sLoad trojan uses BITS to steal data
- CStealer: a new Windows trojan password stealer
- Emotet malware active threat drops IcedID Trojan
