
The Microsoft Threat Intelligence Center (MSTIC) has uncovered a “sophisticated email-based attack” operated by NOBELIUM, as part of a wide-scale malicious email campaign.
The NOBELIUM threat actor is allegedly behind recent cyberattacks against SolarWinds, SUNBURST backdoor, TEARDROP malware and GoldMax malware.
Microsoft tracked the campaign since January of 2021 and has seen the threat evolve into a “series of waves demonstrating significant experimentation.”
“On May 25, 2021, the campaign escalated as NOBELIUM leveraged the legitimate mass-mailing service, Constant Contact, to masquerade as a US-based development organization and distribute malicious URLs to a wide variety of organizations and industry verticals,” Microsoft stated in the blog post.
Moreover, Microsoft outlined details behind the attacker motives, malicious behavior, and best practices to protect against this attack.
The tech giant warned the NOBELIUM campaign is still an “active incident” and has attempted to target close to 3,000 individual accounts across more than 150 entities. The patterns include using infrastructure and tooling against each victim, while going undetected for longer period of time.
“This new wide-scale email campaign leverages the legitimate service Constant Contact to send malicious links that were obscured behind the mailing service’s URL (many email and document services provide a mechanism to simplify the sharing of files, providing insights into who and when links are clicked),” Microsoft added.
Although the high volume of email likely triggered anti-spam and threat detection tools likely was able to block much of the email, some likely got through organizations’ defenses.
Delivery techniques
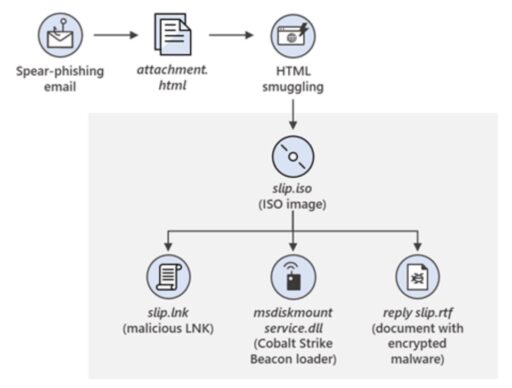
The Microsoft team observed part of the NOBELIUM campaign evolution involved spear-phishing emails with an attached malicious HTML file used to compromise systems.
“When opened by the targeted user, a JavaScript within the HTML wrote an ISO file to disc and encouraged the target to open it, resulting in the ISO file being mounted much like an external or network drive,” Microsoft said.
To add, a shortcut file (LNK) would then execute an accompanying DLL, which would result in the execution of Cobalt Strike Beacon, as illustrated in Figure 1 below:
Microsoft further described other experimentations and techniques used for delivery in the blog post.
Related Articles
- Global active exploits against SolarWinds via Sunburst backdoor
- Microsoft and FireEye reveal new details on SolarWinds cyberattack
- New Supernova malware analysis reveals new APT cyberattack methods against vulnerable SolarWinds infrastructure
- CISA releases new malware analysis on Supernova
- SolarWinds releases updated advisory on SUPERNOVA malware (updated with CVE-2020-10148)
- FireEye publishes Microsoft 365 tools and hardening strategies to defend against SolarWinds attackers
- DHS issues new emergency guidance on SolarWinds Orion Code compromise
- 3 good examples of how to apply the Zero Trust Security Model
