
Microsoft has warned that Nobelium threat actors are using a new backdoor malware dubbed FoggWeb to target Active Directory Federation Services (AD FS) servers.
The Microsoft Threat Intelligence Center (MSTIC) has been working closely with partners and customers to learn more about Nobelium, the group previously behind recent cyberattacks against SolarWinds, SUNBURST backdoor, TEARDROP malware and recent wide-scale malicious email campaign.
In the most recent attacks, Microsoft has observed FoggWeb in the wild since early April 2021.
“NOBELIUM employs multiple tactics to pursue credential theft with the objective of gaining admin-level access to Active Directory Federation Services (AD FS) servers. Once NOBELIUM obtains credentials and successfully compromises a server, the actor relies on that access to maintain persistence and deepen its infiltration using sophisticated malware and tools,” Microsoft wrote in a blog post on Monday.
Microsoft added that FoggWeb is further used to “remotely exfiltrate the configuration database of compromised AD FS servers, decrypted token-signing certificate, and token-decryption certificate, as well as to download and execute additional components.”
FoggyWeb backdoor
In addition to exfiltrating sensitive data from compromised AD FS systems, FoggyWeb also can receive additional malicious components from the actor’s command-and-control (C2) server and then execute commands on the compromised host.
Microsoft also provided a diagram that describes how the bad actor communicates with the FoggyWeb backdoor:
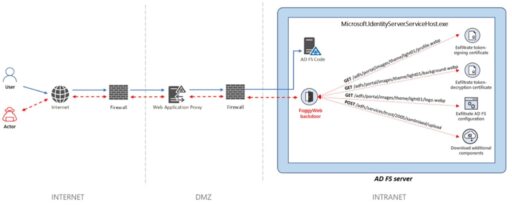
Moreover, FoggyWeb runs under the context of the main AD FS process, so thus inherits the AD FS service account permissions used to access the AD FS configuration database.
Mitigations
Microsoft recommends administrators follow Microsoft’s Best Practices for Securing Active Directory Federation Services to harden systems from potential attacks. These guidelines also include how customers can use a hardware security module (HSM) to prevent the exfiltration of secrets by FoggyWeb.
Finally, readers can also review more information on FoggyWeb in the Microsoft report, which includes more details on the loader, backdoor, indicators of compromise (IoC) and much more.
Related Articles
- Justice Department seizes domains used in Nobelium spear-phishing attacks
- Microsoft uncovers NOBELIUM ‘sophisticated email-based attack’
- Global active exploits against SolarWinds via Sunburst backdoor
- Microsoft and FireEye reveal new details on SolarWinds cyberattack
- New Supernova malware analysis reveals new APT cyberattack methods against vulnerable SolarWinds infrastructure
- CISA releases new malware analysis on Supernova
- SolarWinds releases updated advisory on SUPERNOVA malware (updated with CVE-2020-10148)
- FireEye publishes Microsoft 365 tools and hardening strategies to defend against SolarWinds attackers
- DHS issues new emergency guidance on SolarWinds Orion Code compromise
- 3 good examples of how to apply the Zero Trust Security Model
