
A previously unknown malware family dubbed FontOnLake is targeting Linux systems.
Security researchers from ESET have discovered FontOnLake malware that uses “custom and well-designed modules” that are “constantly under development and provide remote access to the operators, collect credentials, and serve as a proxy server.”
FontOnLake file samples first appeared on VirusTotal in May of 2020 and other samples were uploaded throughout the same year. To add, the uploaded samples and command-and-control (C2) information point to potential Linux system targets in Southeast Asia.
“To collect data (for instance ssh credentials) or conduct other malicious activity, this malware family uses modified legitimate binaries that are adjusted to load further components. In fact, to conceal its existence, FontOnLake’s presence is always accompanied by a rootkit. These binaries such as cat, kill or sshd are commonly used on Linux systems and can additionally serve as a persistence mechanism,” ESET wrote in a blog post.
Moreover, the ESET researchers added that the operators of FontOnLake appear cautious since many of the malware samples appear to connect to non-standard ports on the now inactive C2 servers. The actors also use mostly C/C++ and multiple third party libraries, such as Boost, Poco and Protobuf.
FontOnLake Components
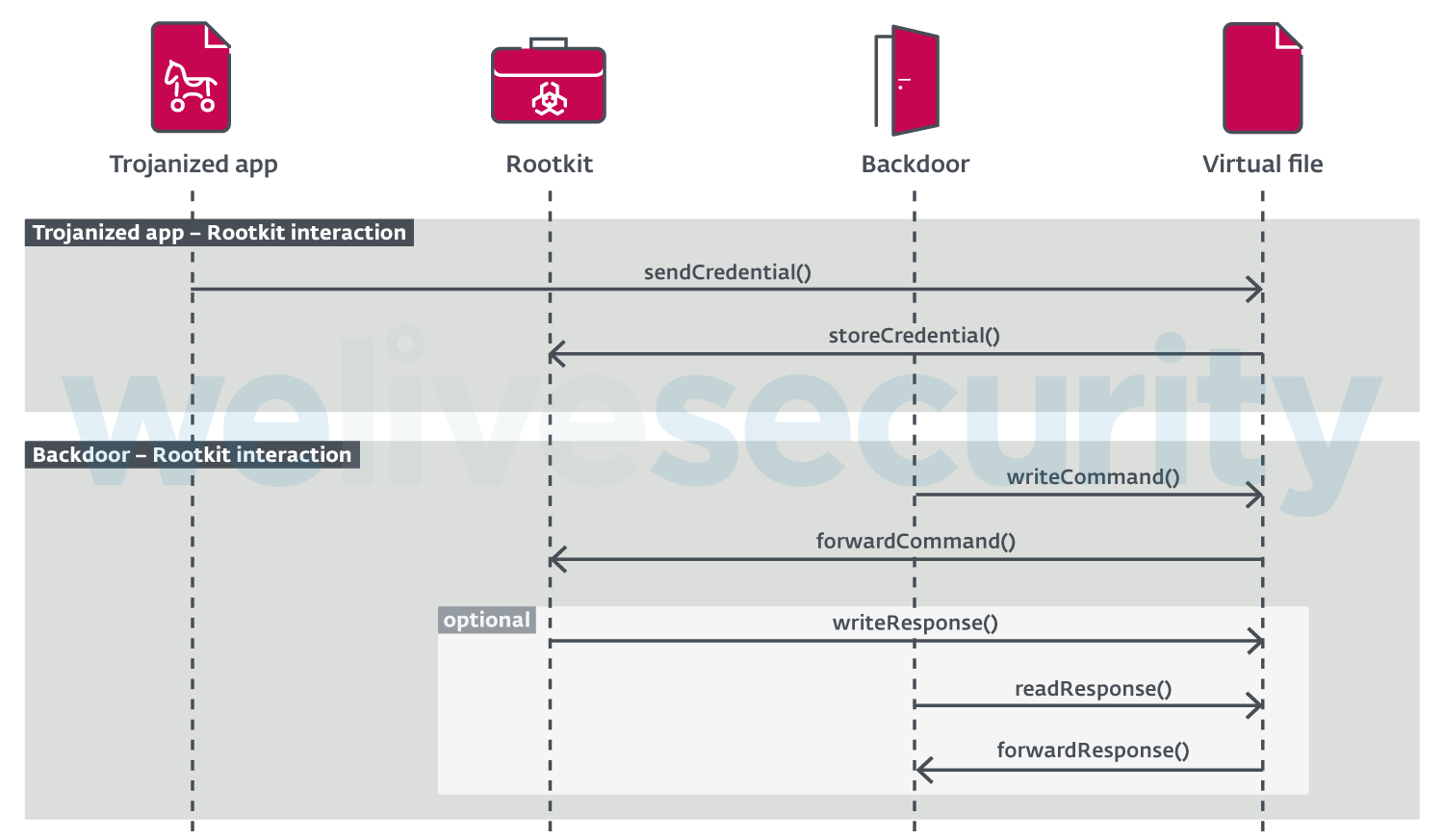
Some of the FontOnLake components include trojanized applications, backdoors and rootkits.
The malicious actors use the trojanized applications to primarily load custom backdoor or rootkit modules. Backdoors are used for primary communication channels. Rootkit kernel mode components hide and disguise their presence, help with code updates, or provide other backdoors used for fallback in the event the primary fails.
In addition, ESET provided a diagram (Figure 1 below) that describes how the components interact:
Finally, readers can check out the ESET blog post for more details on the FontOnLake malware components, as well as indicators of compromise (IoC).
