
Microsoft has released a new report on Nobelium that has been targeting cloud service providers (CSPs), managed service providers (MSPs) and other IT organizations in order to launch broader attacks against customers they serve.
Nobelium is the infamous cybergang behind the Solarwinds attacks in 2020 that shares the same “compromise-one-to-compromise-many” approach used in recent attacks.
Microsoft has analyzed the Nobelium activity targeting organizations in the United States and Europe since May 2021. The actors attempt to exploit the existing trust relationship and privileged access granted to service providers by other organizations.
“Microsoft has observed NOBELIUM targeting privileged accounts of service providers to move laterally in cloud environments, leveraging the trusted relationships to gain access to downstream customers and enable further attacks or access targeted systems. These attacks are not the result of a product security vulnerability but rather a continuation of NOBELIUM’s use of a diverse and dynamic toolkit that includes sophisticated malware, password sprays, supply chain attacks, token theft, API abuse, and spear phishing to compromise user accounts and leverage the access of those accounts. These attacks have highlighted the need for administrators to adopt strict account security practices and take additional measures to secure their environments,” Microsoft explained in the blog post.
As a consequence, the Nobelium actors can then use those compromised systems and credentials to launch multiple attack vectors against downstream customers such as virtual private networks (VPNs) or unique service provider solutions that enable network access.
Moreover, Microsoft provided an example of how Nobelium conducted an intrusion using a variety of attack methods as illustrated in Figure 1 below.
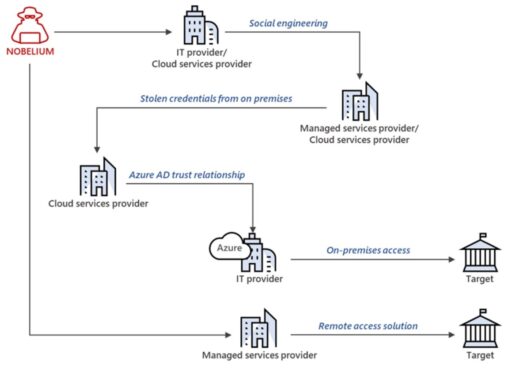
Mitigations
Microsoft recommends the following safeguards to help mitigate and remediate Nobelium threats for Microsoft partners:
- Verify and monitor compliance with Microsoft Partner Center security requirements such as:
- Enforce multi-factor authentication (MFA) and conditional access policies enforced.
- Ensure APIs adopt the Secure Application Model framework.
- Regularly check the “Activity Log” in Partner Center.
- Remove delegated administrative privileges (DAP) connection when not in use
- Conduct a thorough investigation and comprehensive response, to include:
- Review the Azure AD Security Operations Guide
- Check out Microsoft’s best practices to include Incident response playbooks for Phishing and Password spray.
For downstream customers, follow these best practices:
- Review, harden, and monitor all tenant administrator accounts.
- Review service provider permissions access from B2B and local accounts.
- Verify MFA and conditional access enabled.
- Review and audit logs and configurations (e.g., Azure AD sign-ins and configuration changes and review existing log availability and retention strategies).
Finally, organizations should check out the Nobelium observed behaviors, as well as tactics, techniques, and procedures (TTPs) as provided in the Microsoft report.
Related Articles
- Microsoft: Nobelium cybergang deploys FoggyWeb backdoor to target AD FS servers
- Justice Department seizes domains used in Nobelium spear-phishing attacks
- Microsoft uncovers NOBELIUM ‘sophisticated email-based attack’
- New Supernova malware analysis reveals new APT cyberattack methods against vulnerable SolarWinds infrastructure
- Microsoft and FireEye reveal new details on SolarWinds cyberattack
