
Researchers have discovered a new malware threat dubbed “Squirrelwaffle” that uses Microsoft Office documents to infect victim systems with CobaltStrike.
McAfee Labs first observed the Squirrelwaffle malicious doc activity surfaced in September 2021.
The security firm described the infection chain that first started with the typical phishing email with a malicious link hosting the malicious documents.
Once the victim clicks on the link, a ZIP file is downloaded with the malicious document embedded in the file. It then immediately drops a VBS file and script with the obfuscated powershell. The script then invokes further malicious DLLs, which are then executed.
McAfee describes the attack infection chain in the following diagram:
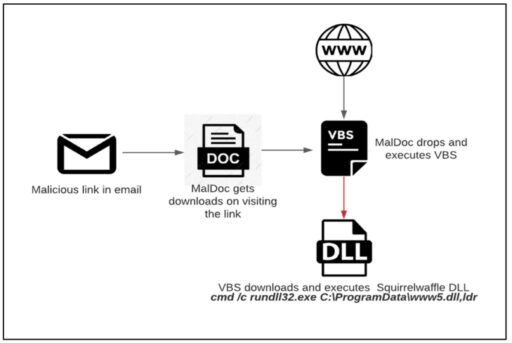
Readers may recall last year in cybersecurity reports when threat actors used “dual use tools” such as CobaltStrike, PowerShell Empire, Powersploit and Metasploit for exploitation and post-exploitation tasks. Such tools were one of the top 3 endpoint threats used in 2020 cyberattacks.
Although many organizations use these tools for penetration tasks and to find vulnerabilities, cyber criminals also frequently use them for malicious activities.
Readers can check out more details on the Squirrelwaffle threat to include malicious doc analysis, VBA script analysis, and indicators of compromise in the McAfee Labs blog post.
Related Articles
- The top 3 endpoint threats used in 2020 cyberattacks – Securezoo Blog
- Babuk ransomware: Soon to be targeting VMware and *nix systems?
- Zloader trojan bypasses Microsoft Office malware-protection defenses
- Zyklon malware campaign targets Office vulnerabilities
- Loda RAT malware campaign
- Emotet malware campaign warning
