An advanced persistent threat (APT) campaign dubbed TiltedTemple has been using a “sophisticated tool” and malicious backdoor SockDetour to target U.S. defense contractors.
According to Palo Alto’s Unit 42 researchers, the TiltedTemple advanced persistent threat (APT) campaign was first discovered with connections to exploits of the Zoho ManageEngine ADSelfService Plus vulnerability CVE-2021-40539 and ServiceDesk Plus vulnerability CVE-2021-44077.
The threat actors used a number of methods to exploit systems and maintain persistence using the backdoor malware SockDetour, likely to have been in the wild since at least July 2019. Primary attacks have been targeted against U.S.-based defense contractors.
SockDetour
The Unit 42 researchers described the SockDetour malware in a recent blog post:
“A custom backdoor, SockDetour is designed to serve as a backup backdoor in case the primary one is removed. It is difficult to detect, since it operates filelessly and socketlessly on compromised Windows servers. One of the command and control (C2) infrastructures that the threat actor used for malware distribution for the TiltedTemple campaign hosted SockDetour along with other miscellaneous tools such as a memory dumping tool and several webshells.”
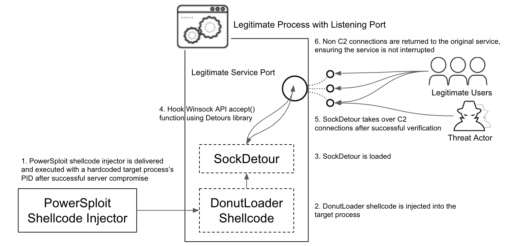
Moreover, the backdoor runs on Windows systems that are running services with listening TCP ports. Once the malware hijacks network connections made to the pre-existing network socket, it then establishes an encrypted C2 channel with the remote threat.
This makes SockDetour more difficult to detect as noted in Figure 1 workflow diagram provided by Unit 42 below:
Compromised QNAP server
What is also interesting is SockDetour was hosted on an FTP server via a compromised Quality Network Appliance Provider (QNAP) small office and home office (SOHO) network-attached storage (NAS) server commonly used in small businesses.
QNAP NAS server vulnerabilities, such as CVE-2021-28799 and CVE-2020-36195, have been known to be targeted by Qlocker and eCh0raix ransomware campaigns.
This is just another reminder to patch these types of systems frequently and as soon as updates are made available.

