In the past month, researchers from FortiLabs have detected a new cyber campaign involving Chinese Advanced Persistent Threat (APT) group Deep Panda that has exploited the Log4Shell (log4j) vulnerability CVE-2021-44228 on vulnerable VMware Horizon servers to install digitally signed Fire Chili rootkits.
Log4Shell is a remote code execution (RCE) vulnerability CVE-2021-44228 caused by Apache Log4j2 JNDI features that do not protect against attacker controlled LDAP and other JNDI related endpoints.
Last December, researchers from LunaSec warned that “many, many services are vulnerable to this exploit,” such as Steam and Apple cloud services, as well as Minecraft and Apache Struts apps. They added similar vulnerabilities were exploited before such as the infamous 2017 Equifax data breach.
Moreover, a proof of concept (PoC) exploit code for Apache Log4j (CVE-2021-44228) had also been published to GitHub.
In the latest attacks, the Deep Panda group exploited the infamous Log4Shell vulnerability in VMware Horizon servers.
“The nature of targeting was opportunistic insofar that multiple infections in several countries and various sectors occurred on the same dates. The victims belong to the financial, academic, cosmetics, and travel industries,” FortiLabs wrote in a blog post.
After exploitation, the Deep Panda actors then deployed a “novel kernel rootkit signed with a stolen digital certificate” on the victim’s vulnerable systems.
As part of the investigation, FortiLabs researchers found a previously unknown Fire Chili rootkit and two compromised digital signatures, one of those directly linked to another Chinese APT group dubbed Winnti.
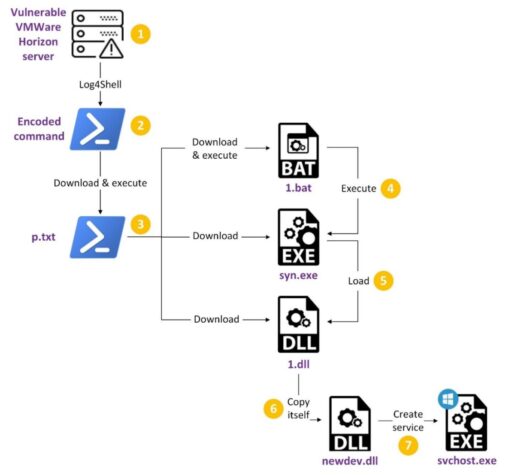
A description of the Log4Shell attack chain is illustrated by FortiLabs in Figure 1:
Earlier this year, threat hunters from CrowdStrike OverWatch group discovered another cyber gang, Aquatic Panda, used Log4Shell exploit tools in recent intrusion attempts against a customer’s vulnerable VMware Horizon instances.
Some of those activities included the execution of bash-based interactive shell with hardcoded IP addresses linked to remote infrastructure managed by the Aquatic Panda threat actors.
In addition, the actors performed reconnaissance operations from the compromised host to obtain current privilege levels as well as system and domain details before downloading scripts and then retrieving malware from their toolkit.
Readers can check out the full threat research report from FortiLabs to include chain of attack, Indicators of Compromise (IoC) and more on the latest Deep Panda threat.

