Threat actors are using a multi-stage malware dubbed ZuoRAT to exploit small office/home office (SOHO) routers and launch sophisticated attacks against North American and European networks.
Researchers from Black Lotus Labs, the threat intelligence arm of Lumen Technologies, discovered ZuoRAT has been targeting a number of SOHO router manufacturers, including ASUS, Cisco, DrayTek, and NETGEAR. However, the cyber experts were only able to fine an exploit script for JCG-Q20 model routers, likely used to exploit vulnerabilities CVE-2020-26878 and CVE-2020-26879.
The script is a Python-compiled Windows portable executable designed to perform command line injection, steal credentials and then download the ZuoRAT agent.
As revealed in a blog post, ZuoRAT “can enumerate a host and internal LAN, capture packets being transmitted over the infected device and perform person-in-the-middle attacks (DNS and HTTPS hijacking based on predefined rules)” (see Figure 1 illustrated by Black Lotus Labs).
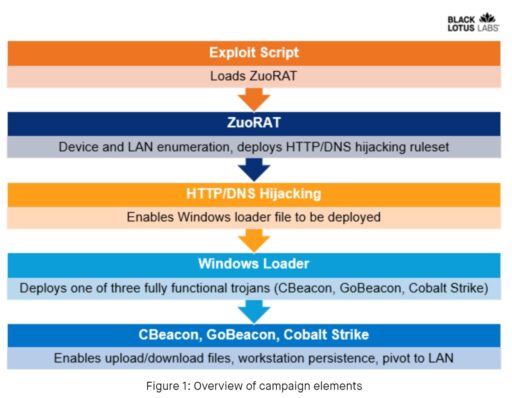
The Windows loader then deploys one of three fully functional second-stage agents (CBeacon, GoBeacon, or Cobalt Strike) depending on the environment.
In the final stage, the trojans can upload/download files such as from the command and control (C2) systems, establish persistence to hide from detection, and then pivot to internal networks.
Readers may recall earlier this year when a similar threat from Sandworm threat actors, used Cyclops Blink malware to target small office/home office (SOHO) routers and network attached storage (NAS) devices.
According to cybersecurity experts in February 2022, Cyclops Blink appeared to be a replacement framework for the VPNFilter malware that was first exposed in 2018 and used to exploit SOHO and NAS devices.
Network defenders should use Indicators of Compromises (IoCs) outlined in the Black Lotus Labs report for more details on how to monitor for suspicious files and activity connecting to suspicious infrastructure.

