The Cybersecurity and Infrastructure Security Agency (CISA) and Federal Bureau of Investigation (FBI) have issued a joint cybersecurity advisory on Zeppelin Ransomware. Bad actors use the Zeppelin ransomware-as-a-service (RaaS) to launch attacks against a wide range of businesses and critical infrastructure organizations.
The Zeppelin ransomware is used to encrypt victims’ files for financial gain and is a derivative of the Delphi-based Vega malware family.
As described in the #StopRansomware: Zeppelin Ransomware alert, the actors have been a threat for nearly three years.
“From 2019 through at least June 2022, actors have used this malware to target a wide range of businesses and critical infrastructure organizations, including defense contractors, educational institutions, manufacturers, technology companies, and especially organizations in the healthcare and medical industries,” CISA explained in the advisory.
Moreover, the actors also request ransomware payments in Bitcoin in the range of thousands to over a million dollars. A ransom note is typically posted on the victim’s compromised system, via the desktop (as noted in Figure 1):
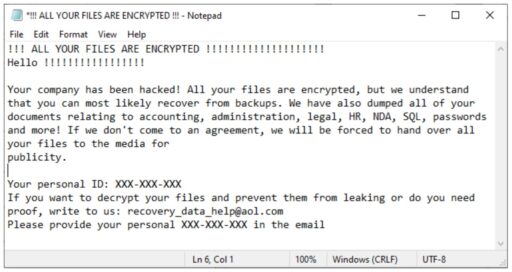
“Prior to deploying Zeppelin ransomware, actors spend one to two weeks mapping or enumerating the victim network to identify data enclaves, including cloud storage and network backups,” CISA added.
The attacks typically involve exploitation of RDP vulnerabilities, SonicWall firewall vulnerabilities, and phishing campaigns.
Readers may also recall back in December 2019 when remote attackers abused ConnectWise Control software to deliver Zeppelin ransomware to its victims.
Check out the full report for more details on indicators of compromise (IoC), attack techniques, recommended mitigations and valuable resources.
Related Articles
- CISA and FBI alert: Attackers actively exploiting vulnerability in Zoho ManageEngine ServiceDesk Plus
- CISA and FBI alert: DarkSide ransomware used in Colonial Pipeline cyberattack (and mitigation guidance) – updated
- APT41 launches broad cyber campaign with multiple exploits
- Guidance for CISOs to improve remote worker security, free access to small business online collaboration tools

