A threat actor has been deploying malicious OAuth apps on compromised cloud tenants to spread spam.
Microsoft researchers have been monitoring the actor, who has likely been operating spam campaign like those used in recent attacks for many years.
“The investigation revealed that the threat actor launched credential stuffing attacks against high-risk accounts that didn’t have multi-factor authentication (MFA) enabled and leveraged the unsecured administrator accounts to gain initial access,” Microsoft explained in a recent blog post.
From there, the bad actor was able to create a malicious OAuth app on the compromised cloud tenant and then added a malicious inbound connector on the email server.
“The actor then used the malicious inbound connector to send spam emails that looked like they originated from the targets’ domain,” Microsoft added.
Microsoft illustrated the attack chain in Figure 1 below.
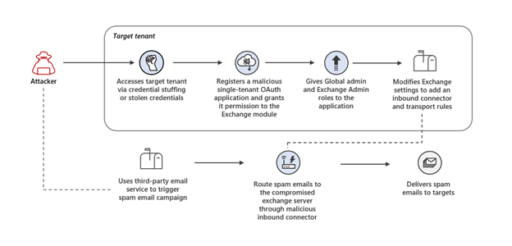
Moreover, Microsoft surmised the attacker likely ran a PowerShell script to perform multiple Azure Active Directory (AAD) management activities via the compromised admin accounts. As a result, the actor was able to more rapidly deploy the malicious OAuth apps.
In addition to creating a new inbound connector, the actor also created transport rules, sets of actions taken on any of the organization’s mail flows (such as deleting specific email headers).
“By deleting these headers, the attacker tried defense evasion to prevent security products or email providers detecting or blocking their emails and increase the success rate of the spam campaign,” Microsoft noted.
In conclusion, the actor’s likely motive was to generate sweepstakes spam emails designed to trick recipients into forking over their payment card details or signing up for fake recurring subscriptions with the expectations of winning big prizes.
Microsoft recommends organizations enable multi-factor authentication (MFA) on all administrator accounts. Entities should also implement conditional access policies (e.g., device compliance or trusted IP address requirements) and continuous access evaluation (e.g., revoking access when a user is terminated or moves to an untrusted location).
Related Articles
- Report: Linux malware and cloud misconfigurations top cybersecurity threats
- Microsoft exposes and disables Polonium activity targeting Israeli organizations
- DevSecOps best practices to secure cloud-native and microservices-based applications
- PRC state-sponsored cyber actors routinely exploit these 16 network device vulnerabilities
- Top 30 most commonly exploited vulnerabilities over 2020 and 2021

