The Microsoft Detection and Response Team (DART) has spotted an increase in attackers using token theft in the cloud to compromise corporate systems while bypassing multi-factor authentication (MFA) and other authentication controls.
“By compromising and replaying a token issued to an identity that has already completed multifactor authentication, the threat actor satisfies the validation of MFA and access is granted to organizational resources accordingly,” Microsoft explained in a blog post.
To obtain a token, users typically sign into a web application (protected by Azure Active Directory or other identity platform) using their credentials. In some cases, organizations will also require users to complete MFA as condition to access resources.
The Microsoft team described two types of attacks used by actors in recent token thefts: AitM phishing and “pass-the-cookie” attacks.
AitM phishing attacks
Microsoft said attackers are increasing using tactics such as adversary-in-the-middle (AitM) phishing attacks or pass-the-cookie attacks in order to bypass MFA controls and steal tokens in lieu of passwords.
“Frameworks like Evilginx2 go far beyond credential phishing, by inserting malicious infrastructure between the user and the legitimate application the user is trying to access. When the user is phished, the malicious infrastructure captures both the credentials of the user, and the token,” Microsoft warned.
As a consequence, attackers can use stolen tokens against users for financial gain or towards privileged administrator accounts to gain administrative control and total tenant compromise (as noted in Figure 1).
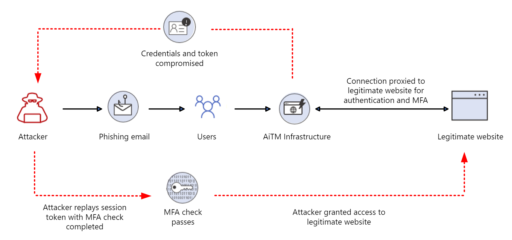
“Pass-the-cookie” attacks
Moreover, Microsoft explained bad actors are using “pass-the-cookie” attacks to bypass authentication controls by compromising browser cookies.
“If an attacker can compromise a device and extract the browser cookies, they could pass that cookie into a separate web browser on another system, bypassing security checkpoints along the way,” Microsoft wrote.
Microsoft further described the “pass-the-cookie” attack workflow in Figure 2:
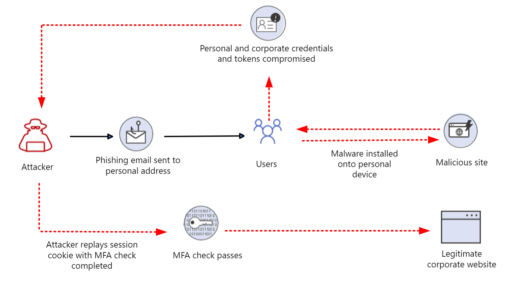
To add, malware such as Emotet, Redline, and IcedID have also been developed to extract and steal browser cookies.
Mitigations
Microsoft further provided multiple good mitigations organizations can leverage to help thwart token stealing threats, for instance:
- Ensure only known devices that adhere to company security policies should be allowed to connect to critical applications.
- Reduce lifetime of sessions and also the viable time of a token.
- Enforce conditional access policies (such as Conditional Access App Control in Microsoft Defender for Cloud Apps).
- Use “phishing resistant MFA solutions” such as FIDO2 security keys, Windows Hello for Business, or certificate-based authentication for users.
“Utilizing compliance tools like Intune in combination with device based conditional access policies can help to keep devices up to date with patches, antivirus definitions, and EDR solutions,” Microsoft added.
Finally, Microsoft suggested adding these types of controls to “applications and users that have the greatest risk to the organization,” such as Global Administrators, Billing Administrators, Finance apps, Human capital management (HCM) apps, and core cloud infrastructure and management tools, just to name a few.

