Attackers have been exploiting a Forta GoAnywhere zero-day vulnerability (CVE-2023-0669).
According to a NIST advisory published on February 6, 2023 (last updated February 15, 2023):
“Fortra (formerly, HelpSystems) GoAnywhere MFT suffers from a pre-authentication command injection vulnerability in the License Response Servlet due to deserializing an arbitrary attacker-controlled object.“
NIST rates the vulnerability CVE-2023-0669 a CVSS score of 7.8.
Fortra has since released a patch (7.1.2) on February 7, 2023 to address this actively exploited vulnerability.
According to a Rapid7 blog post and Mastodon post by Brian Krebs on February 2, 2023, the vulnerability is a remote code injection flaw that requires administrative console access for successful exploitation:
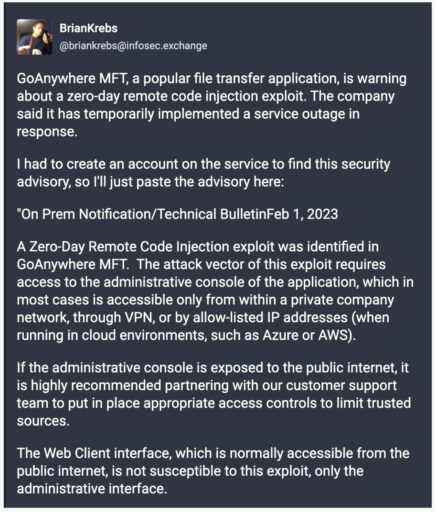
The issue affects on-premise instances of Fortra’s GoAnywhere MFT managed file transfer solution.
AttackerKB also released an update on the issue along with technical analysis.
Related Articles
- Microsoft: RaaS attacks continue to evolve and expand
- CISA adds 2 Microsoft vulnerabilities to Known Exploited Vulnerabilities Catalog (to include 1 Windows zero-day)
- Microsoft January 2023 Security Updates addresses 98 vulnerabilities (11 rated Critical, 1 zero day)
- Microsoft report highlights Mac ransomware threats and techniques
- Apple Fixes Exploited Zero-Day Vulnerability (CVE-2023-23529) in IOS, Safari and macOS

