Researchers from Proofpoint have spotted an advanced persistent threat actor (APT) dubbed TA2541 that has been targeting entities in the aviation industry to distribute AsyncRAT malware.
Proofpoint has tracked the threat actor since 2017 and observed TA2541 has been using similar methods to target victims and then distribute remote access trojans (RATs), like its recent malware choice AsyncRAT, used to remotely control compromised systems.
“TA2541 uses themes related to aviation, transportation, and travel. When Proofpoint first started tracking this actor, the group sent macro-laden Microsoft Word attachments that downloaded the RAT payload. The group pivoted, and now they more frequently send messages with links to cloud services such as Google Drive hosting the payload,” Proofpoint wrote in the blog post.
TA2541 attack chain
Proofpoint described the TA2541 attack chain in Figure A below:
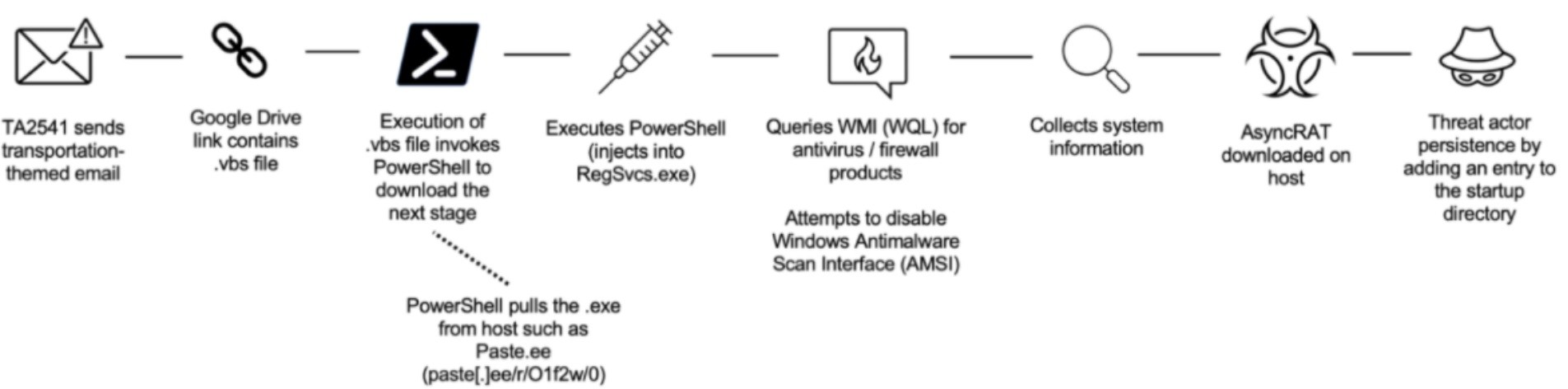
“The threat actor executes PowerShell into various Windows processes and queries Windows Management Instrumentation (WMI) for security products such as antivirus and firewall software, and attempts to disable built-in security protections,” Proofpoint added.
In the next stage, the APT actors will collect system information before downloading the AsyncRAT onto the victim’s system. Other poplular RATs that may be used include NetWire, WSH RAT, and Parallax.
Proofpoint concluded “with high confidence this threat actor will continue using the same TTPs observed in historic activity with minimal change to its lure themes, delivery, and installation,” as well as continue using AsyncRAT, vjw0rm, and other commodity malware in future campaigns.
Other recent RAT campaigns
This past January, the Cisco Talos cybersecurity team also discovered a malicious campaign delivering variants of RATs to include Nanocore, Netwire and Async variants targeting user’s information.
According to Cisco, the threat actor leveraged public cloud services (such as AWS or Azure) to deploy and deliver variants of commodity remote access trojans (RATs) with the information stealing capability starting around Oct. 26, 2021. Campaign victims are primarily distributed across the United States, Italy and Singapore.
