A new report published by Trend Micro revealed that Linux malware and cloud misconfigurations make up some of the top cybersecurity threats facing organizations over the first half of 2022.
Trend Micro’s midyear cybersecurity report, “Defending the Expanding Attack Surface,” highlighted some of the key threats that dominated the first six months of the year, such as malware-as-a-service (MaaS), ransomware-as-a-service (RaaS), cloud misconfigurations, and cryptocurrency mining attacks.
Linux malware
According to the Trend Micro report, ransomware attacks against Linux systems in the first half of 2022 spiked 75% over the first half of 2021.
Last July, LockBit 2.0 ransomware-as-a-service (RaaS) developed and added Linux-based malware used to target vulnerable VMWare ESXi virtual machines. According to a Federal Bureau of Investigation (FBI) alert, the threat actors used both publicly available and custom tools to exfiltrate data followed by encryption using the Lockbit malware.
Moreover, TrendMicro discovered another Linux-based malware variant dubbed Cheerscrypt that targeted ESXi servers and was also based on leaked Babuk source code.
Other RaaS threats
In addition to LockBit, two other Linux malware strains, Conti and BlackCat, also showed a significant increase in RaaS cyberattacks over the previous year, according to Trend Micro’s Smart Protection Network:
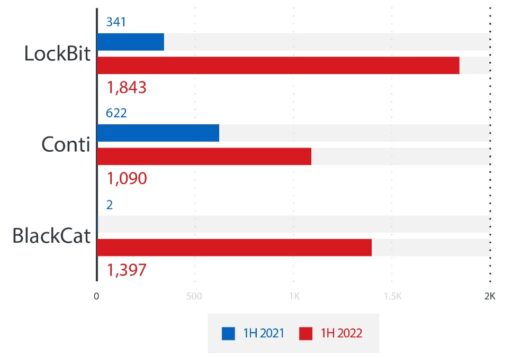
Earlier this year, the FBI had released a report on BlackCat (also known as ALPHV) RaaS, that had compromised at least 60 entities worldwide as of March 2022. BlackCat was also the first ransomware group that had used RUST, a secure programming language designed for performance and reliable concurrent processing.
Cloud misconfigurations
Attackers also looked to actively exploit misconfigurations in cloud-based infrastructure, such as containers and/or Kubernetes deployments.
“In recent years, cloud-based containers have enabled organizations to optimize their processes and development cycles. Because of the ubiquity of these containers and the fact that many such platforms are misconfigured, they continue to be targeted by cybercriminals,” Trend Micro explained in the report.
“Earlier this year, we investigated Kubernetes clusters that were publicly exposed via port 10250 and found that 243,469 cluster nodes were exposed and identified on Shodan. Out of these, approximately 600 nodes returned the ‘200 – OK’ notification when queried,” Trend Micro added.
As a result, an attacker could abuse such nodes by installing malware via the kubelet API.
Readers can also check out the full 50-page Trend Micro report here.
Related Articles
- FBI releases Lockbit 2.0 ransomware-as-a-service IoCs
- FBI: BlackCat ransomware has compromised 60 entities worldwide
- BlackCat: a new ransomware-as-a-service threat
- DevSecOps best practices to secure cloud-native and microservices-based applications
- CISA: Take these urgent steps to protect your organization against potential critical cybersecurity threats
- Mount Locker ransomware targets Windows APIs to spread through networks
- CISA and FBI alert: DarkSide ransomware used in Colonial Pipeline cyberattack (and mitigation guidance)
- Pipeline ransomware attack shuts down 45% of East Coast’s fuel (US passes emergency waiver, systems restarted) – updated
- Threat actors use FiveHands Ransomware and SombRAT in new cyberattack
- Alert: Qlocker and eCh0raix ransomware attacks against QNAP NAS devices

