
Security researchers have discovered a new vulnerability in OpenBSD’s OpenSMTPD mail server. An attacker could exploit the remote code execution vulnerability CVE-2020-7247 and execute arbitrary shell commands with elevated privileges.
OpenSMTPD is part of the OpenBSD project and is a Unix daemon used to implement the Simple Mail Transfer Protocol. To add, OpenSMTPD is used to deliver messages on a local machine or to relay them to SMTP servers.
The Qualys Research Labs security team found the OpenSMTPD vulnerability and published their findings on January 29.
The developers of OpenBSD have already provided a patch for the vulnerability.
“This vulnerability exists in OpenBSD’s mail server OpenSMTPD’s “smtp_mailaddr()” function, and affects OpenBSD version 6.6. This allows an attacker to execute arbitrary shell commands like “sleep 66” as root user,” Animesh Jain said in the blog post.
In addition, Qualys also confirmed the vulnerability has been exploitable since 2018 as noted in Figure 1 below.
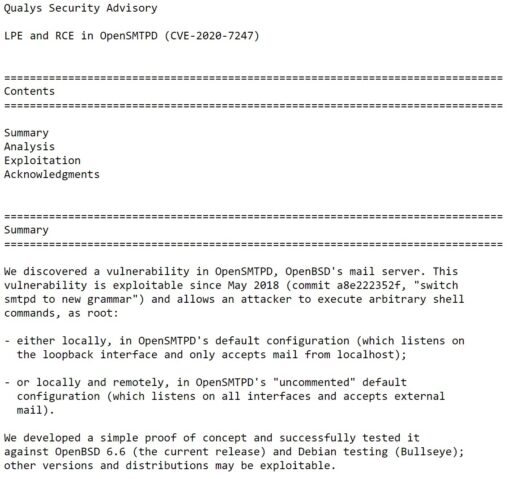
Organizations and users are encouraged to upgrade their OpenBSD systems to OpenBSD 6.6.
