
The National Security Agency (NSA) has issued new guidance for adopting encrypted DNS over HTTPS dubbed “DoH.”
The NSA released an information sheet with new guidelines on adopting DoH, short for Domain Name System (DNS) over Hypertext Transfer Protocol over Transport Layer Security (HTTPS).
According to the guidelines, DoH offers additional DNS security controls to help prevent “many initial access, command and control, and exfiltration techniques used by threat actors.”
DNS is critical for the internet to function in that it translates domain names (e.g., “nsa.gov”) to Internet Protocol addresses.
In the past, these DNS lookups were not encrypted. However, DoH encrypts DNS requests by using HTTPS to ensure privacy, integrity and the “last mile” of source authentication with a client’s DNS resolver. In addition, DoH can help prevent eavesdropping and unauthorized manipulation of DNS traffic.
“The enterprise DNS resolver may be either an enterprise-operated DNS server or an externally hosted service. Either way, the enterprise resolver should support encrypted DNS requests, such as DoH, for local privacy and integrity protections, but all other encrypted DNS resolvers should be disabled and blocked,” the NSA explained in the DNS guidelines PDF.
“However, if the enterprise DNS resolver does not support DoH, the enterprise DNS resolver should still be used and all encrypted DNS should be disabled and blocked until encrypted DNS capabilities can be fully integrated into the enterprise DNS infrastructure.”
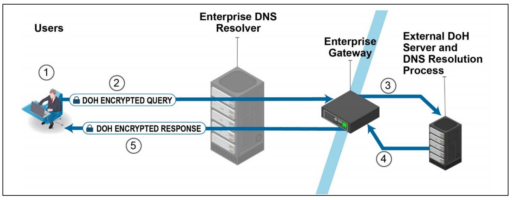
Moreover, the NSA describes how DoH works in conjunction with internal and external DNS resolvers in Figure A below.
DoH benefits
According to the NSA guidelines, DoH protects DNS traffic between a client and a DNS resolver from unauthorized access to data by cyber threat actors.
“Since the traffic is encrypted and blends in with other HTTPS traffic to websites, it is difficult for cyber threat actors to determine which packets contain DNS requests or responses and see which domains and IP addresses were requested,” the NSA explained.
“The responses from the DNS resolver are also authenticated and protected from unauthorized modification. In contrast, traditional DNS transactions occur in plaintext on a port that is exclusively used for DNS, so cyber threat actors can easily read and modify the traditional DNS traffic.”
Readers should review the entire paper for more information pertaining DoH-related issues to look out for, such as configurations, monitoring and exploitations of upstream DNS traffic, just to name a few.
