
Security researchers have discovered seven Dnsmasq vulnerabilities that open up many network and Linux devices to DNS cache poisoning attacks or remote code execution.
Dnsmasq is a popular open-source DNS forwarding software and is used for caching Domain Name System (DNS) responses.
Israeli security firm JSOF discovered the Dnsmasq vulnerabilities, collectively dubbed “DNSpooq” that may affect nearly 40 vendors who use dnsmasq in their products.
According to a JSOF blog post, DNSpooq consists of two types of vulnerabilities:
- DNS cache poisoning attacks (vulnerabilities identified as CVE-2020-25686, CVE-2020-25684 and CVE-2020-25685).
- Buffer overflow vulnerabilities (identified as CVE-2020-25687, CVE-2020-25683, CVE-2020-25682 and CVE-2020-25681).
DNS cache poisoning
Three DNS cache poisoning vulnerabilities have been identified as CVE-2020-25686, CVE-2020-25684 and CVE-2020-25685.
“This type of attack allows subverting of DNS queries in an organization or device using dnsmasq. Essentially, this means that an attacker will be able to reroute communications made by a specific target that relies on a website name,” JSOF explained.
As a consequence, the attacker can pull off different kinds of fraud by diverting victim traffic (such as internet browsing, emails, SSH, remote desktop, software updates, etc.) to malicious websites.
Moreover, JSOF has provided sample diagram in Figure 1 below on how DNS cache poisoning works.
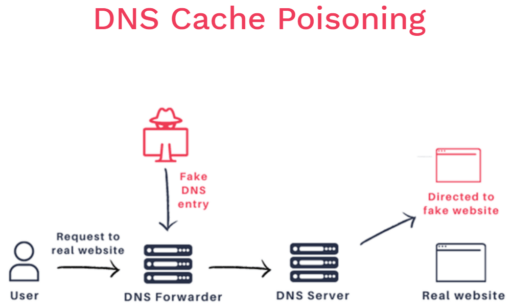
Buffer overflow vulnerabilities
Four buffer overflow vulnerabilities have been identified: CVE-2020-25687, CVE-2020-25683, CVE-2020-25682 and CVE-2020-25681.
These include a High severity heap-based buffer overflow vulnerability that could result in remote code execution if dnsmasq is configured to use DNSSEC. To add, some of these could also lead to denial of service condition as well.
JSOF mentioned that each of the buffer overflow vulnerabilities pose limited risk by itself, but can lead to more “potent attack” when combined with the cache-poisoning vulnerabilities.
Vendor updates
In addition, JSOF provided a table listing 40 vendors and respective products that use Dnsmasq and could be impacted by the DNSpooq vulnerabilities.
Two of the notable vendors that also released new advisories on DNSpooq include Cisco and Red Hat.
At the time of publication, Cisco said none of their products were affected by the four buffer overflow vulnerabilities. However, the tech giant confirmed multiple Cisco products have been found to be susceptible to DNS cache poisoning attacks.
In addition, Red Hat confirmed systems running Red Hat Enterprise Linux 8 (in the non-default configuration) is impacted by the buffer overflow vulnerabilities if DNSSEC is configured. Red Hat Enterprise Linux 6, 7 and 8 versions are all vulnerable to the DNS cache poisoning attacks.
