
Security researchers have discovered nine vulnerabilities collectively dubbed NAME:WRECK than can break DNS implementations in TCP/IP stacks and lead to denial of service or remote code execution. The experts also provided guidance to organization on how to fix the issues.
In new research published by Forescout Research Labs and JSOF Research Labs, the security experts provided details on the NAME:WRECK vulnerabilities that affect Domain Name System (DNS) implementations. These vulnerabilities impact popular IT software (FreeBSD) and IoT/OT firmware, such as Siemens’ Nucleus NET.
Forescout and JSOF estimated “at least 100 million devices are impacted” by NAME:WRECK and further warned the “widespread deployment and often external exposure of vulnerable DNS clients leads to a dramatically increased attack surface.”
The team further discovered that half of the DNS implementations of message compression in seven new TCP/IP stacks are vulnerable as well.
NAME:WRECK vulnerabilities
The security report highlights each of the NAME:WRECK vulnerabilities that we have summarized below (along affected stack, description and CVSS score). Readers can also check out the full report for more details.
- Critical RCE CVE-2016-20009 (IPnet): The DNS client has a stack-based overflow on the message decompression function leading to a potential RCE (CVSS score 9.8).
- Critical RCE CVE-2020-15795 (Nucleus NET): The DNS domain name label parsing functionality does not properly validate the names in DNS responses (CVSS score 8.1).
- Critical RCE CVE-2020-27009 (Nucleus NET): The DNS domain name record decompression functionality does not properly validate the pointer offset values (CVSS score 8.1).
- High DoS CVE-2020-7461 (FreeBSD): The vulnerability exists due to a boundary error when parsing option 119 data in DHCP packets in dhclient(8) (CVSS score 7.8).
- Medium DoS CVE-2020-27736 (Nucleus NET): The DNS domain name label parsing functionality does not properly validate the name in DNS responses (CVSS score 6.5).
- Medium DoS CVE-2020-27737 (Nucleus NET): The DNS response parsing functionality does not properly validate various length and counts of the records (CVSS score 6.5).
- Medium DoS CVE-2020-27738 (Nucleus NET): The DNS domain name record decompression functionality does not properly validate the pointer offset values (CVSS score 6.5).
- Medium DNS Cache Poisoning CVE-2021-25677 (Nucleus NET): The DNS client does not properly randomize DNS transaction ID (TXID) and UDP port numbers, allowing attackers to perform DNS cache poisoning/spoofing attacks (CVSS score 5.3).
- Medium DoS (no CVE available) for NetX: Affects multiple functions in the DNS resolver component (CVSS score 6.5).
The three Critical vulnerabilities and one High severity bug (CVE-2020-7461) can result in remote code execution (RCE). The remaining Medium severity vulnerabilities could result in Denial of Service (DoS) or DNS cache poisoning.
Furthermore, the report highlights one of the common attack scenarios as illustrated in Figure 1 below:
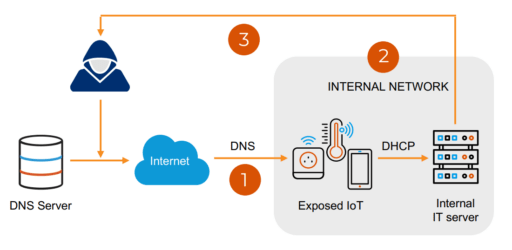
In this example, an attacker can exploit NAME:WRECK vulnerabilities on internal and external targets, such as IoT devices used as entry points, pivot to internal servers and then exfiltrate data.
General mitigations
To reduce the potential impact to NAME:WRECK threat, the report advised organizations limit the network exposure of critical vulnerable devices via network segmentation, use internal DNS servers, and patch devices in a timely manner.
FreeBSD, Nucleus NET and NetX have all been recently patched. Device vendors that use this same software should also provide updates as well.
Previous DNS and TCP/IP stack threats
Readers may recall previous DNS and TCP/IP stack vulnerabilities that gained quite a bit of attention in 2020 such as Ripple20 and SIGRed.
Moreover, researchers also recently discovered DNSpooq, a collection of Dnsmasq vulnerabilities that affected nearly 40 vendors who use dnsmasq in their products. Many of those vulnerabilities could have opened up many network and Linux devices to DNS cache poisoning attacks or remote code execution.
Related Articles
- Ripple20 zero-day vulnerabilities impact hundreds of millions of IoT devices
- DNSpooq: Dnsmasq vulnerabilities open up network and Linux devices to attack
- Microsoft July 2020 Security Updates and patch for ‘Wormable’ RCE Vulnerability in Window DNS Server (includes SIGRed)
- NSA issues new guidance on encrypted DNS
