
A security researcher has discovered a seven-year old polkit privileged escalation vulnerability CVE-2021-3560 that could allow a remote attacker root shell access on Linux systems.
polkit is a system service associated with systemd and is used to control system-wide privileges in Linux-based operating systems. It also enables non-privileged processes running on Linux systems to communicate with privileged processes.
GitHub Security Lab researcher Kevin Backhouse discovered the polkit privileged escalation vulnerability CVE-2021-3560. After responsibly disclosing the bug with the polkit maintainers and Red Hat, a patch was released on June 3, 2021. The CVE is rated High severity and sports a CVSS base score of 7.8.
Backhouse first sent out a tweet regarding the threat on June 7:
A few days later, GitHub followed up with a tweet pointing to a new blog post on the polkit vulnerability, along with an exploitation demo video, on June 10:
“The vulnerability is triggered by starting a dbus-send command but killing it while polkit is still in the middle of processing the request,” Backhouse wrote.
Backhouse further described the polkit architecture in Figure 1 below:
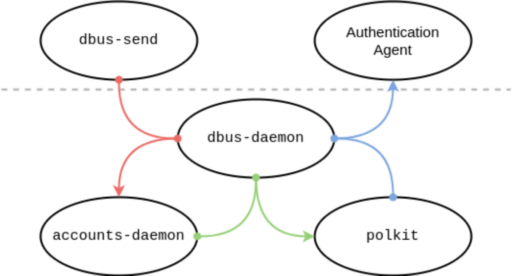
The two processes above the dotted line are the unprivileged process, that communicate to the privileged processes at bottom of the diagram via dbus-daemon.
Backhouse described a sequence of nine steps the process should follow. In one of the steps, however, if polkit asks “dbus-daemon for the UID of connection :1.96,” it does not handle the error correctly.
“In fact, polkit mishandles the error in a particularly unfortunate way: rather than rejecting the request, it treats the request as though it came from a process with UID 0. In other words, it immediately authorizes the request because it thinks the request has come from a root process,” Backhouse said.
In conclusion, the researcher recommended Linux administrators update their Linux systems as soon as possible since the vulnerability is “very simple and quick to exploit.” Installed polkit version 0.113 (or later) is vulnerable and affects popular Linux distributions, such as RHEL 8 and Ubuntu 20.04.
Related Articles
- DNSpooq: Dnsmasq vulnerabilities open up network and Linux devices to attack
- Godlua Backdoor targets Linux and Windows systems
- “SACK Panic” Linux vulnerabilities
- Botnet malware targets Linux systems and cloud management tools
- Kobalos Linux malware targets high performance cluster computers
- FreakOut malware exploits new Linux vulnerabilities
