
Researchers have discovered the first known malware dubbed “Siloscape” targeting Windows containers.
Daniel Prizmant of Palo Alto Network’s Unit 42 security group published new research on Siloscape, pronounced as “silo escape,” that aims to open a backdoor into poorly configured Kubernetes clusters and steal user credentials and data.
“Compromising an entire cluster is much more severe than compromising an individual container, as a cluster could run multiple cloud applications whereas an individual container usually runs a single cloud application,” Prizmant wrote in a blog post.
Moreover, the Unit 42 group warned Siloscape is stealthy and uses “sophisticated code obfuscation techniques” to communicate to its command and control (C2) server over Tor networks.
In summary, Prizmant described the malware has these common behaviors and techniques:
- Targets common cloud apps with known exploits in the wild.
- Escapes container to gain code execution on the node.
- Attempts to abuse the node’s credentials and spread in the cluster.
- Uses Tor network to connect to C2 server via IRC protocol.
- Waits for additional commands.
The malware execution flow is further described in Figure 1:
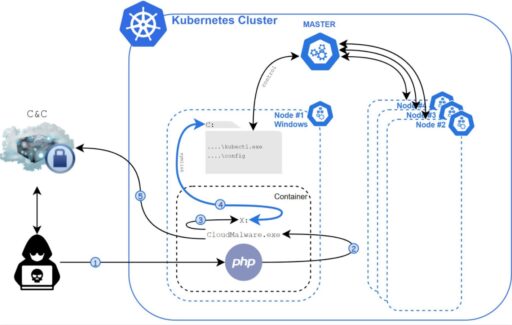
The attacks typically start by exploiting a known vulnerability (such as PHP web vulnerability) and then executes the container malware as it communicates to the C2 server to get its command line arguments.
Next, Siloscape will impersonate CExecSvc.exe to getSeTcbPrivilege privileges and then execute a series of multiple steps to stay undetected, untraceable and then open a backdoor to the Kubernetes cluster.
In conclusion, Prizmant recommends administrators run applications on Hyper-V Windows containers and also make sure the Kubernetes cluster is securely configured.
“In particular, a secured Kubernetes cluster won’t be as vulnerable to this specific malware as the nodes’ privileges won’t suffice to create new deployments. In this case, Siloscape will exit,” Prizmant added.
Readers can also check out Kubernetes Securing a Cluster and also the National Institute of Standards and Technology (NIST) Special Publication (SP 800-190) Application Container Security Guide for additional guidance on how to secure clusters and containers, respectively.
