The Microsoft April 2022 Security Updates includes patches and advisories for 117 vulnerabilities, ten of those rated Critical and two zero-day flaws.
A remote attacker could exploit some of these vulnerabilities to take control of unpatched systems.
In all, the Microsoft security updates address vulnerabilities in the following products, features and roles:
- .NET Framework
- Active Directory Domain Services
- Azure SDK
- Azure Site Recovery
- LDAP – Lightweight Directory Access Protocol
- Microsoft Bluetooth Driver
- Microsoft Dynamics
- Microsoft Edge (Chromium-based)
- Microsoft Graphics Component
- Microsoft Local Security Authority Server (lsasrv)
- Microsoft Office Excel
- Microsoft Office SharePoint
- Microsoft Windows ALPC
- Microsoft Windows Codecs Library
- Microsoft Windows Media Foundation
- Power BI
- Role: DNS Server
- Role: Windows Hyper-V
- Skype for Business
- Visual Studio
- Visual Studio Code
- Windows Ancillary Function Driver for WinSock
- Windows App Store
- Windows AppX Package Manager
- Windows Cluster Client Failover
- Windows Cluster Shared Volume (CSV)
- Windows Common Log File System Driver
- Windows Defender
- Windows DWM Core Library
- Windows Endpoint Configuration Manager
- Windows Fax Compose Form
- Windows Feedback Hub
- Windows File Explorer
- Windows File Server
- Windows Installer
- Windows iSCSI Target Service
- Windows Kerberos
- Windows Kernel
- Windows Local Security Authority Subsystem Service
- Windows Media
- Windows Network File System
- Windows PowerShell
- Windows Print Spooler Components
- Windows RDP
- Windows Remote Procedure Call Runtime
- Windows schannel
- Windows SMB
- Windows Telephony Server
- Windows Upgrade Assistant
- Windows User Profile Service
- Windows Win32K
- Windows Work Folder Service
- YARP reverse proxy
Vulnerability Breakdown
Microsoft patched 117 vulnerabilities to include Elevation of Privilege (46), Remote Code Execution (46), Information Disclosure (13), Denial of Service (9), and Spoofing (3) issues.
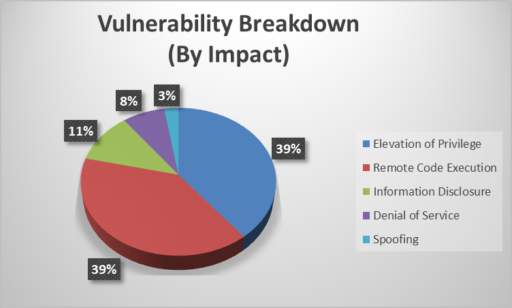
As noted in Figure 1, Elevation of Privilege (EoP) and Remote Code Execution (RCE) vulnerabilities each contributed to 39% of the total vulnerabilities patched this month.
Zero-day vulnerabilities
Of special note, Microsoft patched two zero-day vulnerabilities (CVE-2022-24521 and CVE-2022-26904):
- CVE-2022-24521: Windows Common Log File System Driver Elevation of Privilege (EoP) Vulnerability
- CVE-2022-26904: Windows User Profile Service Elevation of Privilege (EoP) Vulnerability.
Microsoft has confirmed the first EoP vulnerability CVE-2022-24521 has been actively exploited in the wild. The second EoP issue (CVE-26904) is “more likely” to be exploited.
RCE vulnerabilities
Microsoft also addressed ten Critical remote code execution (RCE) vulnerabilities:
- CVE-2022-22008: Windows Hyper-V Remote Code Execution Vulnerability (CVSS 7.8)
- CVE-2022-23257: Windows Hyper-V Remote Code Execution Vulnerability (CVSS 8.8)
- CVE-2022-23259: Microsoft Dynamics 365 (on-premises) Remote Code Execution Vulnerability (CVSS 8.8)
- CVE-2022-24491: Windows Network File System Remote Code Execution Vulnerability (CVSS 9.8)
- CVE-2022-24497: Windows Network File System Remote Code Execution Vulnerability (CVSS 9.8)
- CVE-2022-24500: Windows SMB Remote Code Execution Vulnerability (CVSS 8.8)
- CVE-2022-24537: Windows Hyper-V Remote Code Execution Vulnerability (CVSS 7.8)
- CVE-2022-24541: Windows Server Service Remote Code Execution Vulnerability (CVSS 8.8)
- CVE-2022-26809: Remote Procedure Call Runtime Remote Code Execution Vulnerability (CVSS 9.8)
- CVE-2022-26919: Windows LDAP Remote Code Execution Vulnerability (CVSS 8.1)
The two Network File System (NFS) vulnerabilities (CVE-2022-24491 and CVE-2022-24497) are “more likely to be exploited” and could allow an attacker to “send a specially crafted NFS protocol network message to a vulnerable Windows machine, which could enable remote code execution.”
Moreover, the Remote Procedure Call Runtime RCE vulnerability (CVE-2022-26809) also is more likely to be exploited.
Other security updates
In addition to the Critical RCEs and zero-day vulnerabilities, Microsoft also patched an additional 102 vulnerabilities on April 12, 2022 across multiple products rated “Important” or “Moderate.” The tech giant also addressed 28 Microsoft Edge (Chromium-based) vulnerabilities.
Finally, readers can review the April 2022 Security Updates Release Notes and also download more vulnerability and patch details via Microsoft’s Security Update Guide.
Related Articles
- CISA adds Critical WatchGuard and Microsoft AD flaws to Catalog of exploited vulnerabilities
- Microsoft March 2022 Security Updates (fixes for 71 vulnerabilities, 3 Critical)
- Microsoft warns of destructive MBR wiper malware targeting Ukranian organizations
- NotLegit: 4-year old Microsoft Azure App Service 0-day vulnerability affects source code repositories

