Over the past six months, Microsoft has observed a spike in cyberactivity of 254% from XorDdos, a trojan targeting Linux-based cloud systems and Internet of Things (IoT) devices.
XorDdos was first discovered in 2014 by research group MalwareMustDie and is notable for its denial-of-service-related activities and use of XOR-based encrypted communications.
As part of Secure Shell (SSH) brute force attacks, XorDdos typically uses a malicious shell script to guess credentials and gain access to targeted Linux devices.
“By compromising IoT and other internet-connected devices, XorDdos amasses botnets that can be used to carry out distributed denial-of-service (DDoS) attacks,” Microsoft wrote in a blog post.
Moreover, DDoS attacks can be highly disruptive and also used to hide further malicious activities, such as exploiting systems or infecting systems with malware.
Microsoft further described XorDdos as “robust and stealthy” malware to evade detection:
“Its evasion capabilities include obfuscating the malware’s activities, evading rule-based detection mechanisms and hash-based malicious file lookup, as well as using anti-forensic techniques to break process tree-based analysis.”
Microsoft further illustrated XorDdos attack vector in Figure A below.
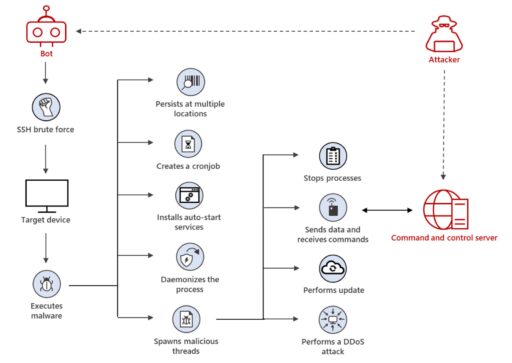
Microsoft also found devices first infected with XorDdos were later infected with other malware, such as Tsunami backdoor.
Readers can check out more details from Microsoft on XorDdos payload analysis, hunting queries, indicators of compromise, and more in the report.
Related Articles
- XORDDoS and Kaiji DDoS botnets target internet exposed Docker servers
- FritzFrog P2P botnet breaches SSH servers
- Doki malware targets exposed Docker servers in the cloud

