Researchers have discovered a new malware threat dubbed Raspberry Robin that uses the Tor network to deliver payloads to Telecom and Government targets.
Trend Micro described the malware threat in a recent blog post:
“Our initial analysis of the malware, which compromised a number of organizations toward the end of September, showed that while the main malware routine contains both the real and fake payloads, it loads the fake payload once it detects sandboxing tools to evade security and analytics tools from detecting and studying the malware’s real routine. Meanwhile, the real payload remains obfuscated under packing layers and subsequently connects to the Tor network.”
Moreover, Trend Micro identified the campaign and malware as Raspberry Robin by Red Canary. The malware has been spreading to telecommunications and government office systems since the beginning of September. The malware spreads to targets with worm-like capabilities through the use of LNK (.lnk) files and an infected USB.
Trend Micro further described the infection routine in the following flow diagram (Figure 1):
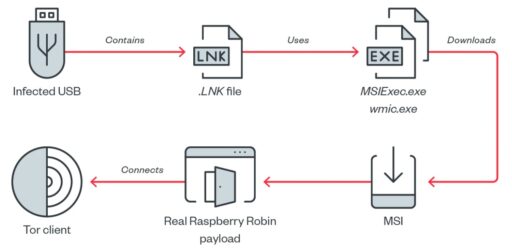
According to the flow, once the user connects the infected USB to the system, Raspberry Robin initially arrives as a shortcut or LNK file.
The LNK file contains a command line that runs a legitimate executable (such as msiexec.exe or wmic.exe) to download a Windows Installer (MSI) package.
To add, when a user double-clicks the LNK file, the Windows Shell “opens” the shortcut file, which then executes an executable file (or cmd.exe).
Finally, when the malware is then downloaded, it is treated as an MSI file and then subsequently loaded by the legitimate executable file on the victim machine.
Readers can check out the full report to learn more about the Raspberry Robin malware threat characteristics, code obfuscation, payloads, and use of Tor client.
Related Articles
- MCCrash botnet launches DDoS attacks against Minecraft servers
- XorDdos: DDoS malware targets Linux systems
- Zerobot botnet exploits 21 vulnerabilities to breach targets
- Mirai variant MooBot botnet targets multiple D-Link flaws
- Emotet botnet reemerges with new threat behaviors
- Agenda Ransomware gang uses Rust to target more companies worldwide
- ‘Achilles’ vulnerability exploit bypasses macOS Gatekeeper

