Researchers from Trend Micro have discovered a way bad actors can abuse a GitHub Codespaces feature to deliver malware.
GitHub Codespaces is a cloud-based development environment that developers can use to customize their project by committing configuration files to their repository (aka “Configuration-as-Code”) that creates a repeatable codespace configuration for all users of their project.
GitHub announced Codespaces on November 10, 2022 and is now generally available for all users. Barriers to entry are also low, since developers can create at least two codespace instances for free.
According to Trend Micro, one of the Codespaces features used for code development and collaboration, sharing forwarded ports publicly, can be exploited by malicious actors and then used to abuse legitimate GitHub accounts to create a malware file server.
“In the process, these abused environments will not be flagged as malicious or suspicious even as it serves malicious content (such as scripts, malware, and ransomware, among others), and organizations may consider these events as benign or false positives,” Trend Micro wrote in a blog post.
Attack methods
In the report, Trend Micro explained how developers have the option to share forwarded ports privately within the organization or publicly.
If the ports are shared publicly, then an attacker can then abuse the feature without authentication controls to host malicious malware and scripts.
“To validate our hypothesis of threat modeling abuse scenario, we ran a Python-based HTTP server on port 8080, forwarded and exposed the port publicly. In the process, we easily found the URL and the absence of cookies for authentication,” Trend Micro added.
Moreover, Trend Micro described how an attacker can use dev containers and a simple script to create open directories on GitHub Codespaces to serve malware as described in Figure 1 below.
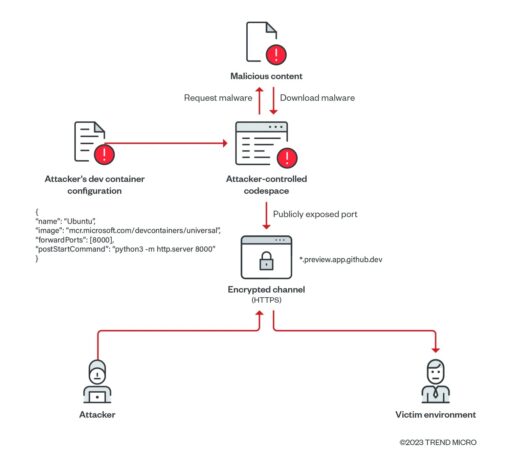
Each created codespace also has a unique identifier and subdomain associated with it. As a result, an attacker can create multiple different instances of open directories, each for a maximum of 30 days.
Although bad actors have been abusing and exploiting free cloud platforms and services for awhile now, the difference in these attacks is the abuse of legitimate accounts and domains that may make it harder to flag as malicious. As a result, new proof of concepts (POCs) are likely right around the corner.
“In a scenario abusing this POC, the attacker can manipulate the publicly shared port to infiltrate and deploy malicious content in a victim’s environment since the domain associated with the exposed port is unique and likely have never been flagged by security tools,” Trend Micro concluded.
Related Articles
- Okta’s GitHub source code repositories hacked
- Okta investigating reports of data breach by Lapsus$ ransomware cybercriminal group (updated)
- Microsoft: Attackers are increasingly using token theft in cyberattacks to bypass MFA
- Misconfigured Microsoft endpoint exposes sensitive data from 65K entities
- Threat actor deploys malicious OAuth apps on compromised cloud tenants to spread spam

