Vice Society ransomware gang has been targeting manufacturing firms in Brazil, Argentina, Switzerland, and Israel.
According to new research by Trend Micro, the group has been using their own custom-built ransomware while still leveraging toolsets such as Cobalt Strike and malware (e.g., Zeppelin and Hello Kitty/FiveHands) to enhance their routines.
Previously, Vice Society has been known to exploit entities in the healthcare and education industries. The group has also been spotted exploiting the PrintNightmare vulnerability in their routines.
Trend Micro also discovered the group is developing new capabilities in late 2022.
“More recently, Vice Society has been able to develop its own custom ransomware builder and adopt more robust encryption methods. This, and any further enhancements, could mean that the group is preparing for their own ransomware-as-a-service (RaaS) operation,” Trend Micro wrote in a blog post.
Vice Society evolution
Trend Micro provided a timeline of the Vice Society evolution that started in early January 2021 through November 2022 in Figure 1.
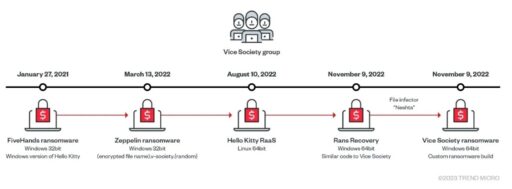
The group first deployed FiveHands ransomware in 2021 and then Zeppelin (2022), Hello Kitty (2022), and more recently their own custom ransomware on November 2022.
Trend Micro also described the workflow in Figure 2 below.
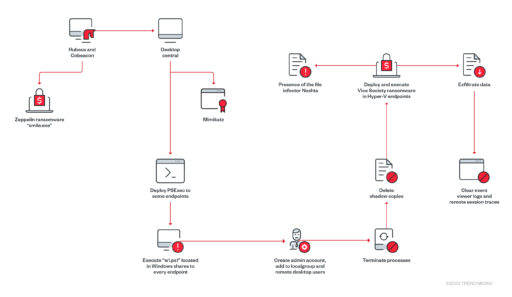
“The arrival vector likely involves the exploitation of a public-facing website or abuse of compromised remote desktop protocol (RDP) credentials,” Trend Micro added.
In addition, Vice Society uses Cobalt Strike as its primary weaponized tool to remotely access and control infected endpoints. Other tools used include Rubeus C# toolset (for raw Kerberos interaction and abuse), as well as Mimikatz to dump passwords and help move laterally within the target’s network.
Readers can check out the Trend Micro post for more details regarding the technical and historic analysis on the Vice Society ransomware threat, as well as related articles below.
Related Articles
- Microsoft patches PrintNightmare vulnerability
- PrintNightmare: Windows Print Spooler service RCE vulnerability exploit code
- Squirrelwaffle uses Office docs to infect victim systems with CobaltStrike
- ZuoRAT targets SOHO devices to launch sophisticated multi-stage cyber attacks
- FBI: BlackCat ransomware has compromised 60 entities worldwide
- Zeppelin Ransomware threatens wide range of businesses and critical infrastructure organizations
- Attackers abuse ConnectWise Control software to deliver Zeppelin ransomware
- Threat actors use FiveHands Ransomware and SombRAT in new cyberattack

